
Log monitoring: A complete guide
Read more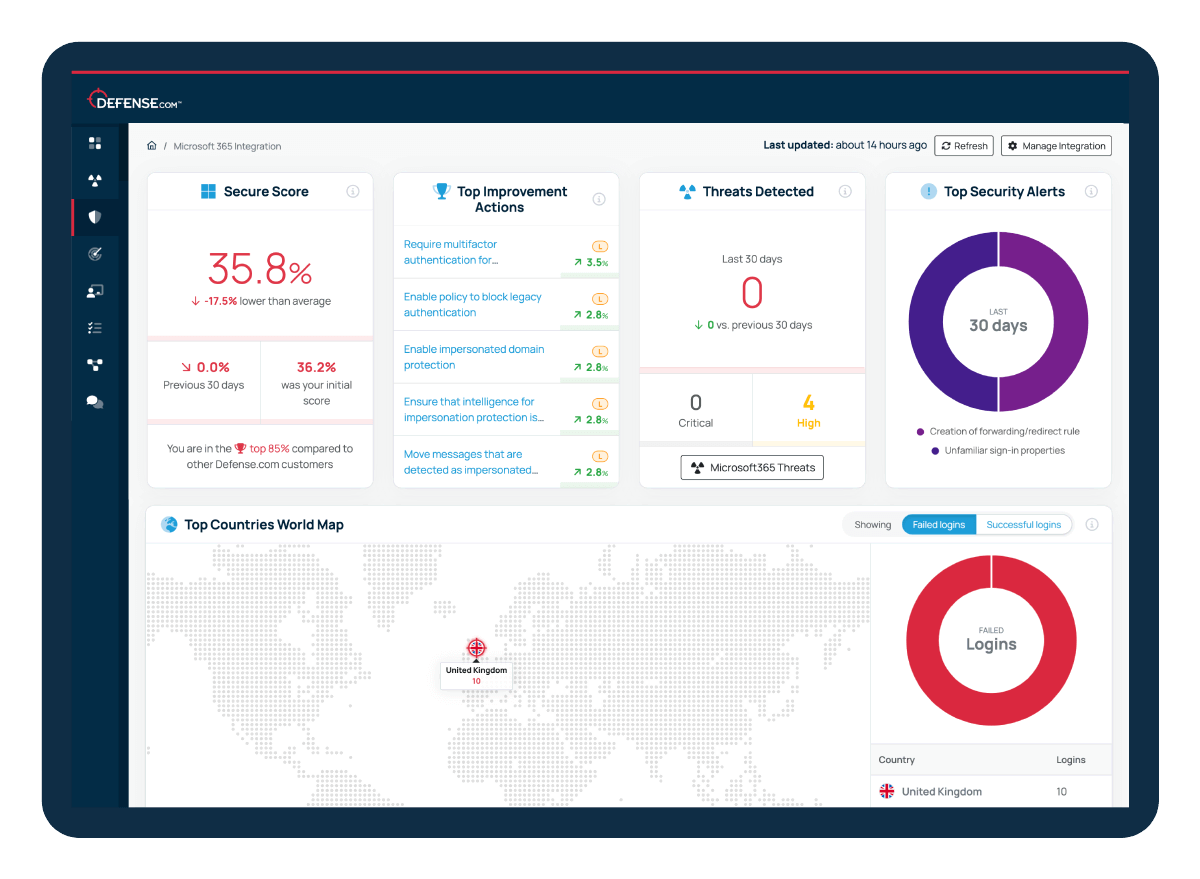
Make your cyber security easier to manage by integrating your Microsoft 365 account with Defense.com.
Instead of switching between multiple portals in Microsoft 365, with Defense.com you can simplify your security operations by combining all alerts from Microsoft 365, and all other vendors in your environment, into one prioritised list.
Try for free



























See how to monitor your secure score, get real-time alerts, and action security improvements – all from a single dashboard. This quick demo shows you exactly how Defense.com simplifies Microsoft 365 security management.
Collect logs and security alerts from your Microsoft 365 account and users to detect malicious activity faster.
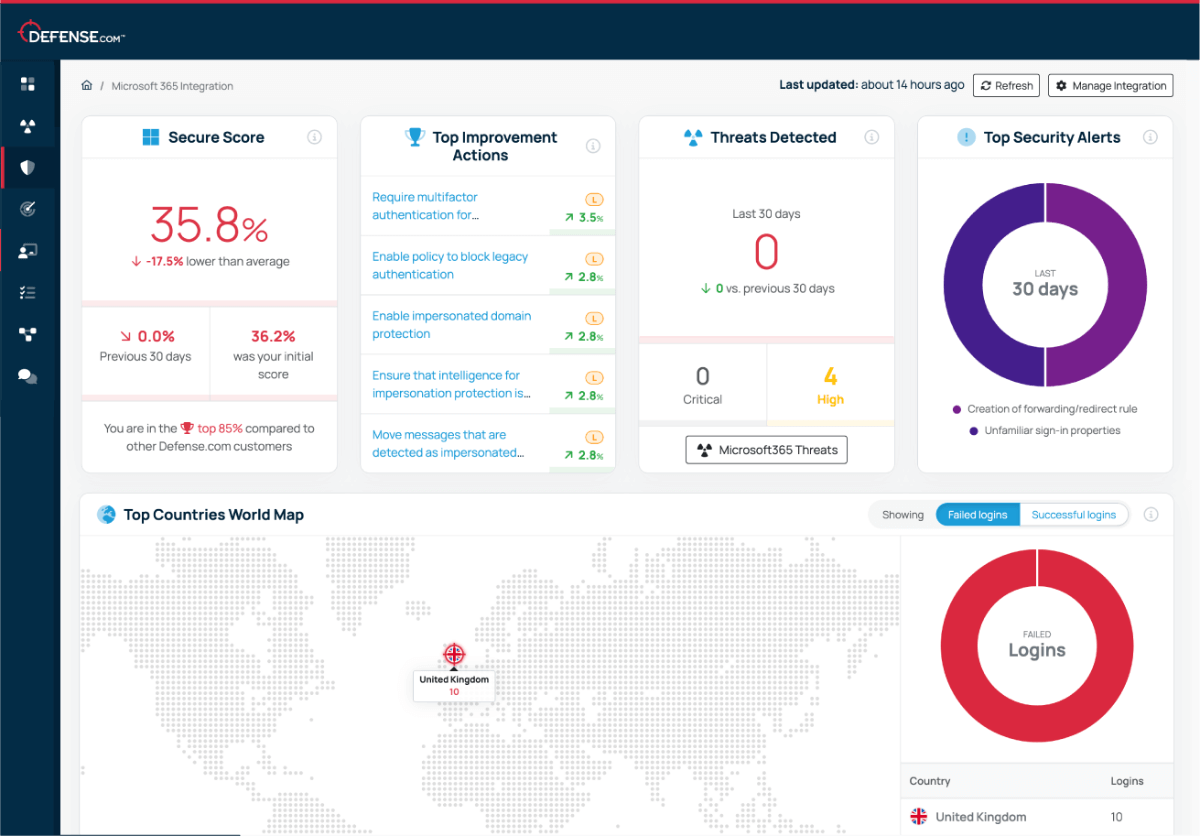
Get instant alerts to new security threats and vulnerabilities affecting your business. Take immediate action by disabling users who pose a risk without leaving Defense.com.
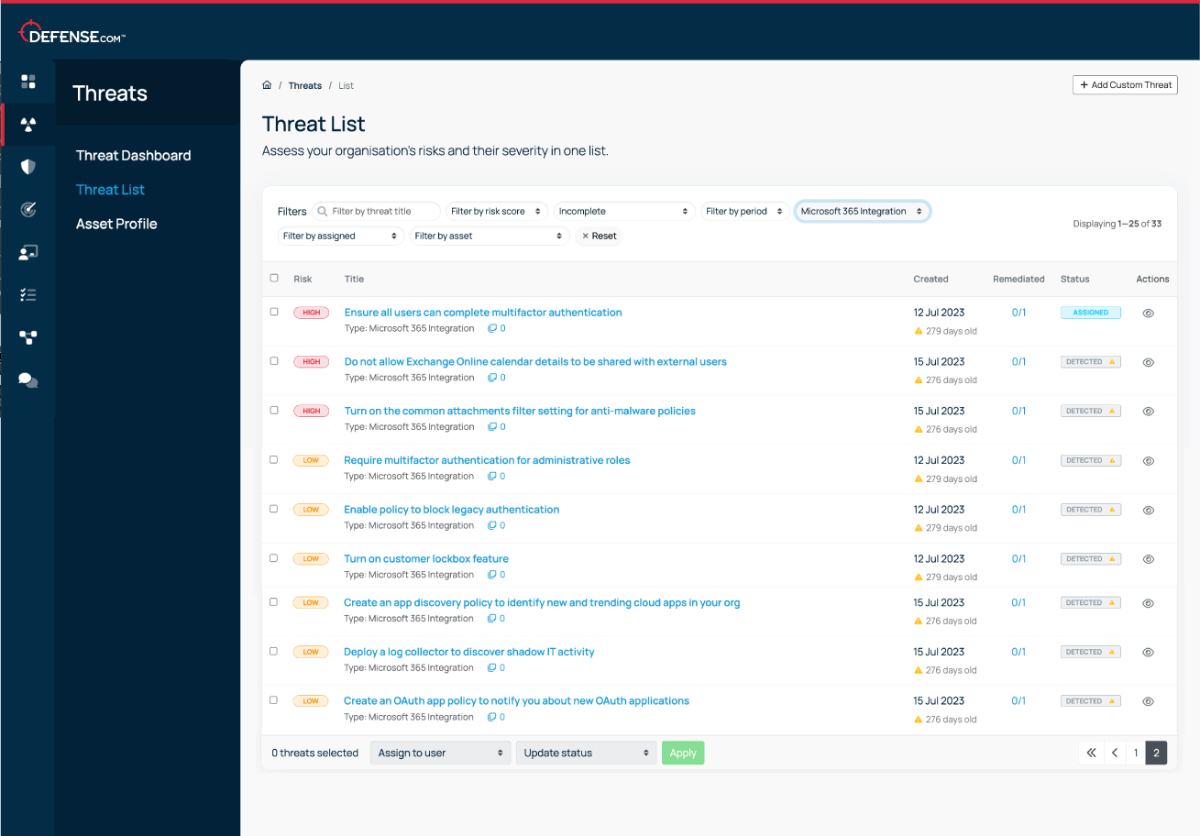
Two-way syncing with Microsoft makes it easy to manage and remediate threats in one place.
Make threat management easier by combining telemetry from your whole security stack in one place.

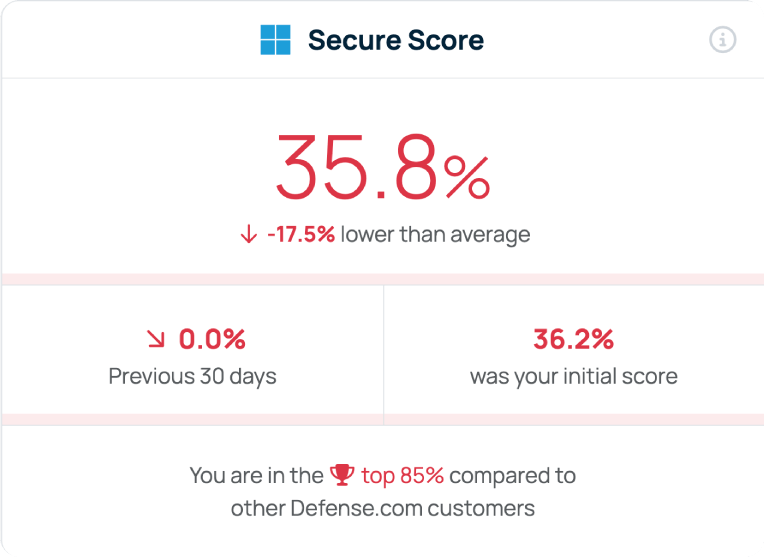
Strengthen your security with clear threat remediation advice and actions to improve your Microsoft Secure Score.
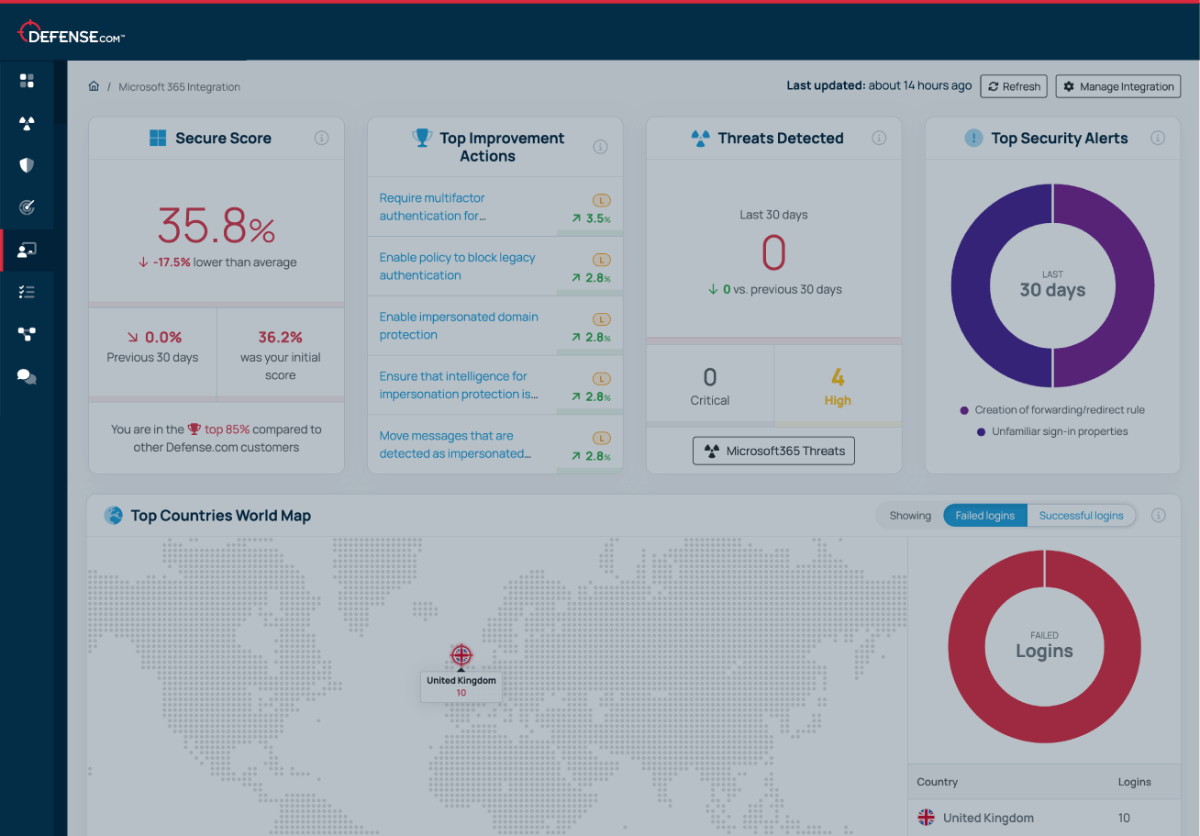



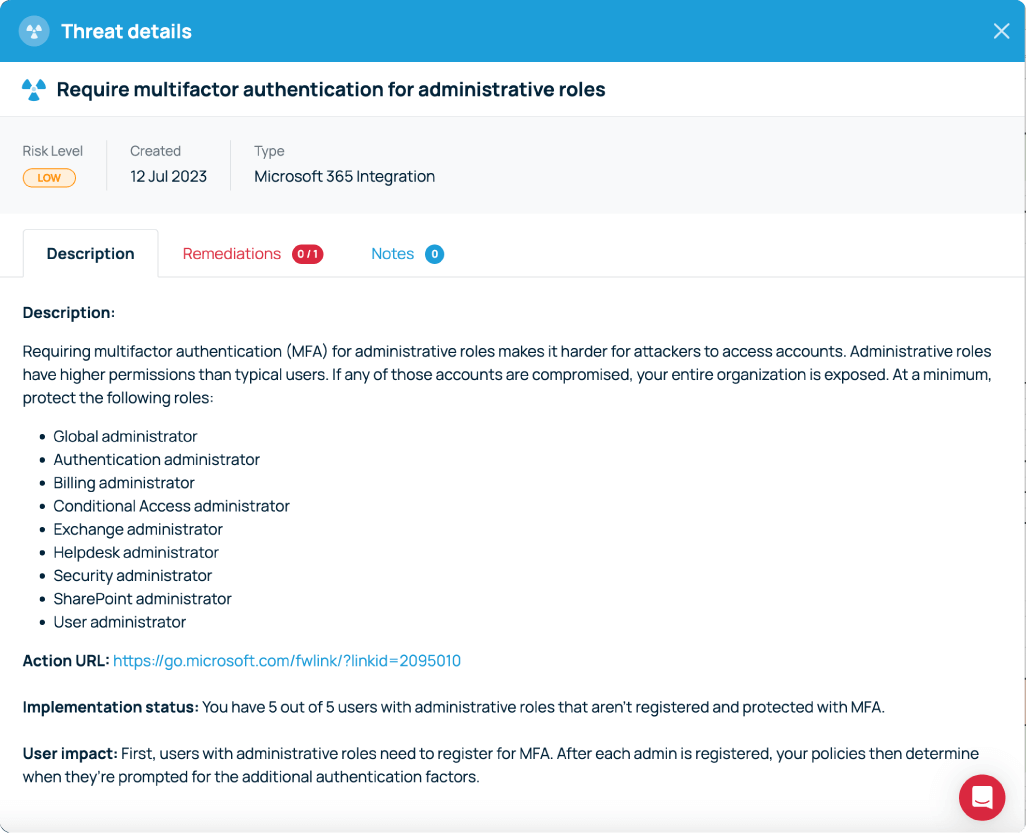


We believe that good cyber security doesn’t have to be complicated. That’s why Defense.com provides you with the detection and response capabilities to effectively reduce your cyber risk.
By combining security tools that identify threats across your environment, Defense.com enables you to prioritise and manage cyber threats with ease. Remediation advice provided by experienced security analysts ensures threats are dealt with quickly and efficiently.

The following audit logs are supported from Microsoft Office 365 and Entra ID (Azure AD):
The following alert sources are also supported:
Setting up your Microsoft 365 integration in Defense.com is quick and easy. Once you’ve set up your Defense.com account, a step-by-step setup wizard will take you through the process.
To complete this integration you’ll need access to your Azure administration account via portal.azure.com and appropriate permissions (such as Global Administrator or Application Developer) to create and manage app registrations.
You can view our detailed Microsoft 365 Integration help guide.
There aren’t any! You can bring logs and security alerts from all Microsoft 365 solutions outlined in this help guide. There is no limit on log volumes, alert volumes or number of Microsoft 365 users.
This integration uses the Microsoft Graph API to gather telemetry directly from Microsoft 365, and therefore does not require any additional logging agents to be installed.
As part of a full Defense.com SIEM deployment, we will also bring in logs and security alerts from many more products (not just Microsoft) to build a better picture of your overall security posture. This will require various logging agents to collect telemetry from local devices and other API calls for cloud systems. A Defense.com SIEM deployment is not required to use the Microsoft 365 integration.
When you mark a Microsoft 365 threat as ‘Remediated’ in Defense.com it will automatically update this threat in your Microsoft 365 account. You will see this in your Microsoft account as 'remediated by a third party'.
Conversely, once you have made the necessary changes and remediated issues in Microsoft 365, this will automatically update in your Defense.com account, too. Any configuration changes in Microsoft 365 that affect your Microsoft Secure Score will also be automatically reflected in your Defense.com account.
Get actionable cyber security advice and insights straight to your inbox.