
10 things you should know about cyber security
Read more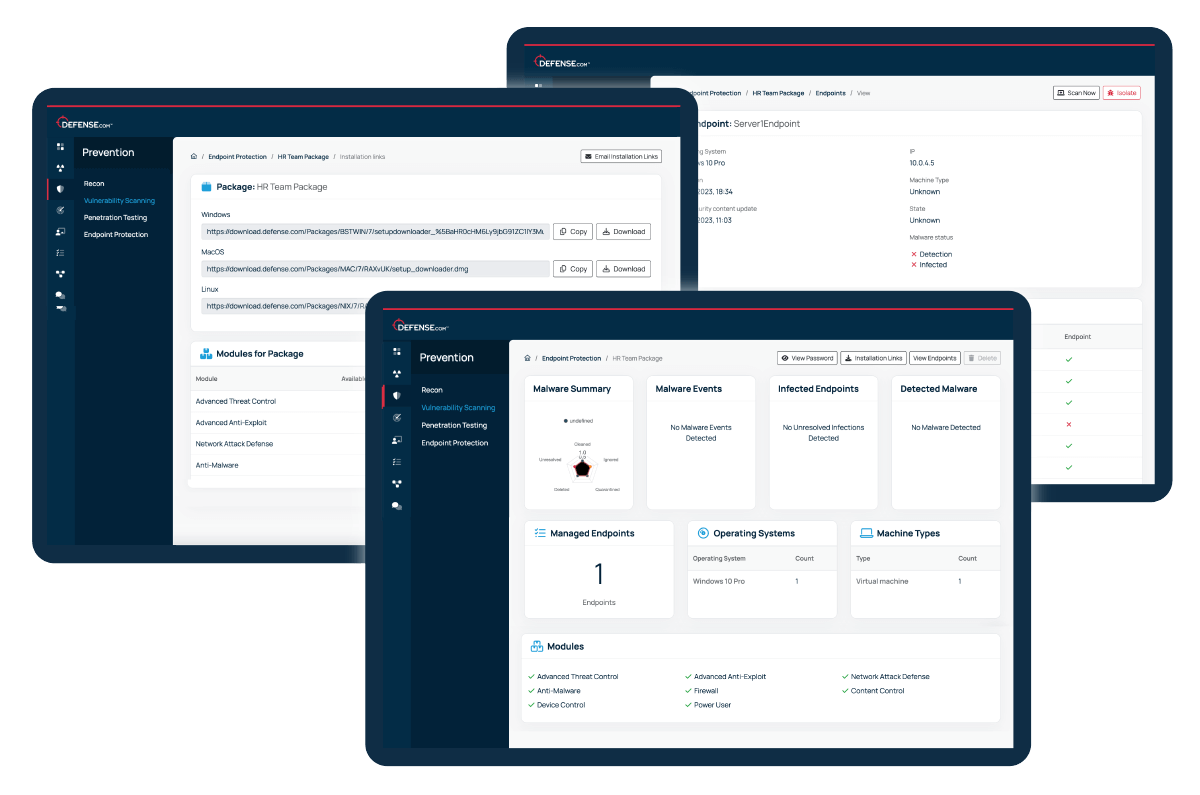
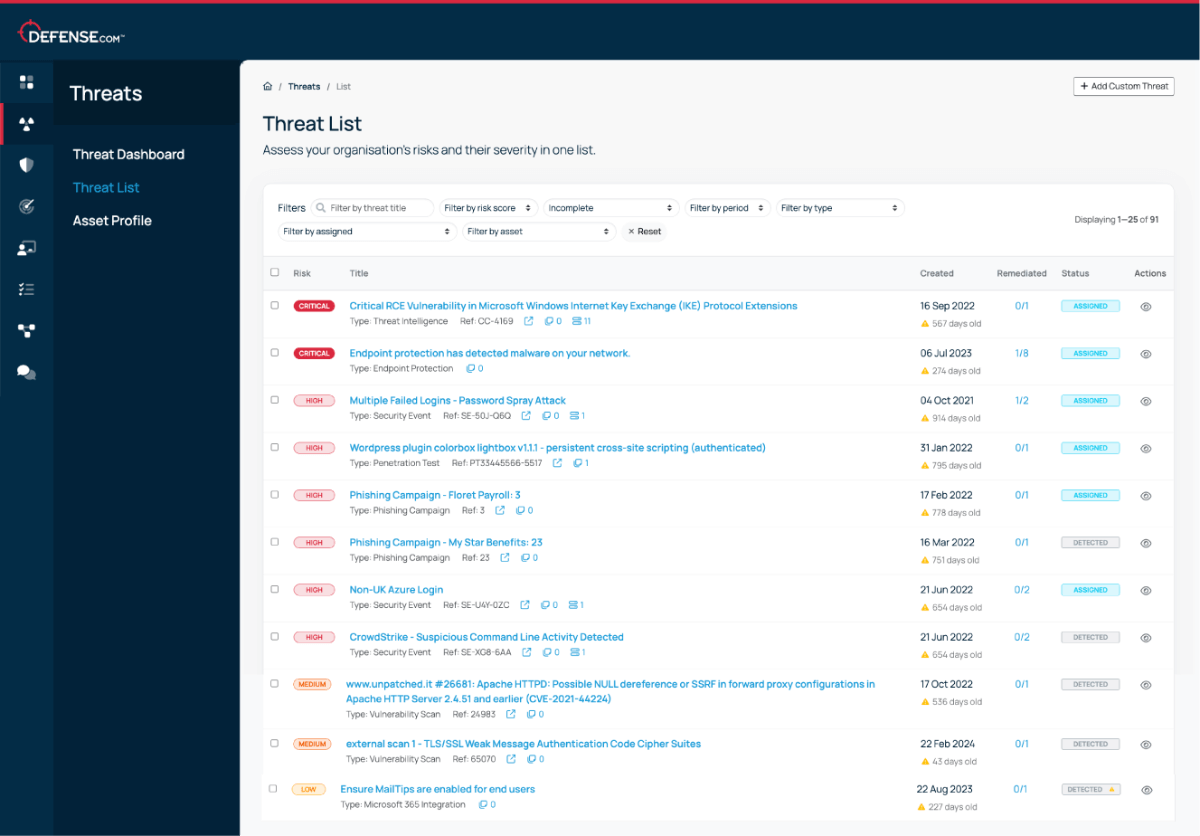
Defense.com EDR proactively discovers threats in real-time. Stay protected against advanced threats including fileless attacks, ransomware and zero-day exploits.
Your endpoints will be continuously monitored for specific indicators of attack (IoAs), MITRE ATT&CK techniques, and other artifacts to discover early-stage attacks.
Try for free



























See how you can deploy real-time endpoint protection, manage device security policies, and respond to threats instantly – from blocking malicious files to isolating compromised devices.
Easily deploy lightweight endpoint protection agents to your Windows, MacOS and Linux devices via remote or manual installation.
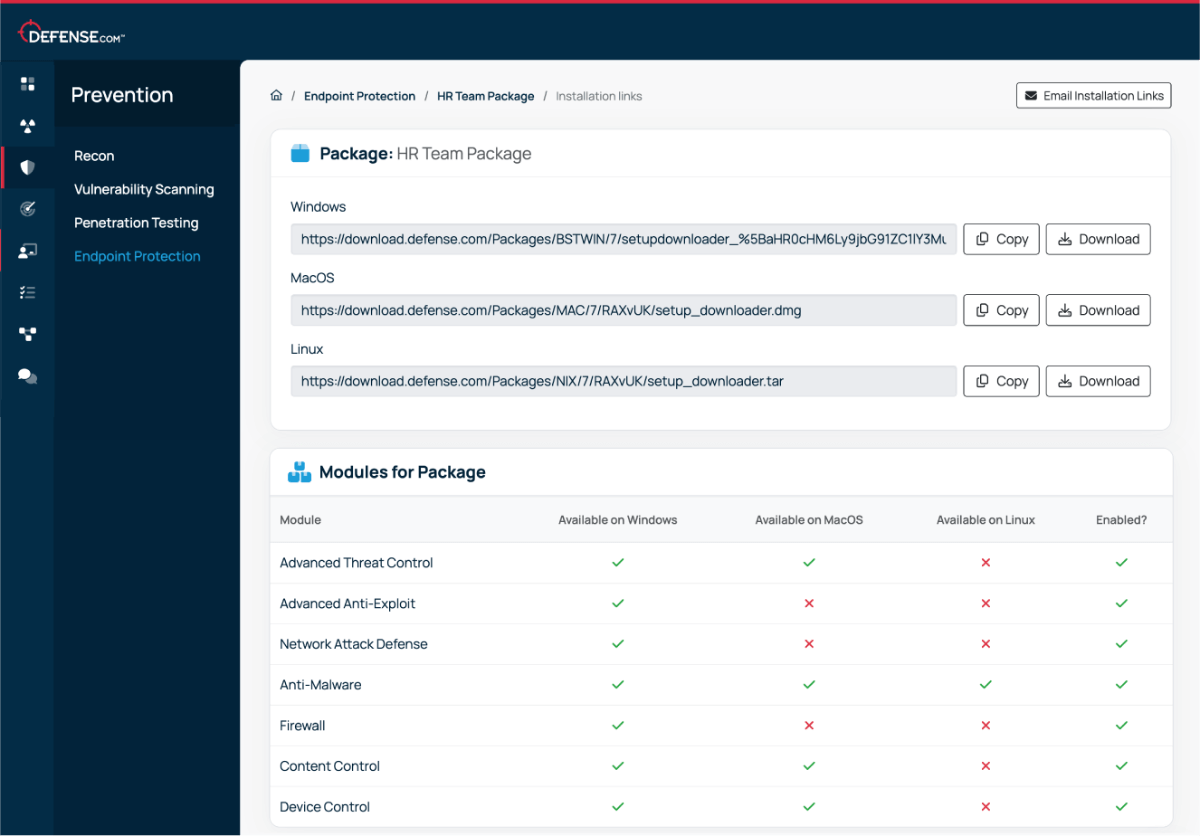
Instantly detect and block threats with a range of modules including anti-malware, firewall, content control, device control and advanced anti-exploit.
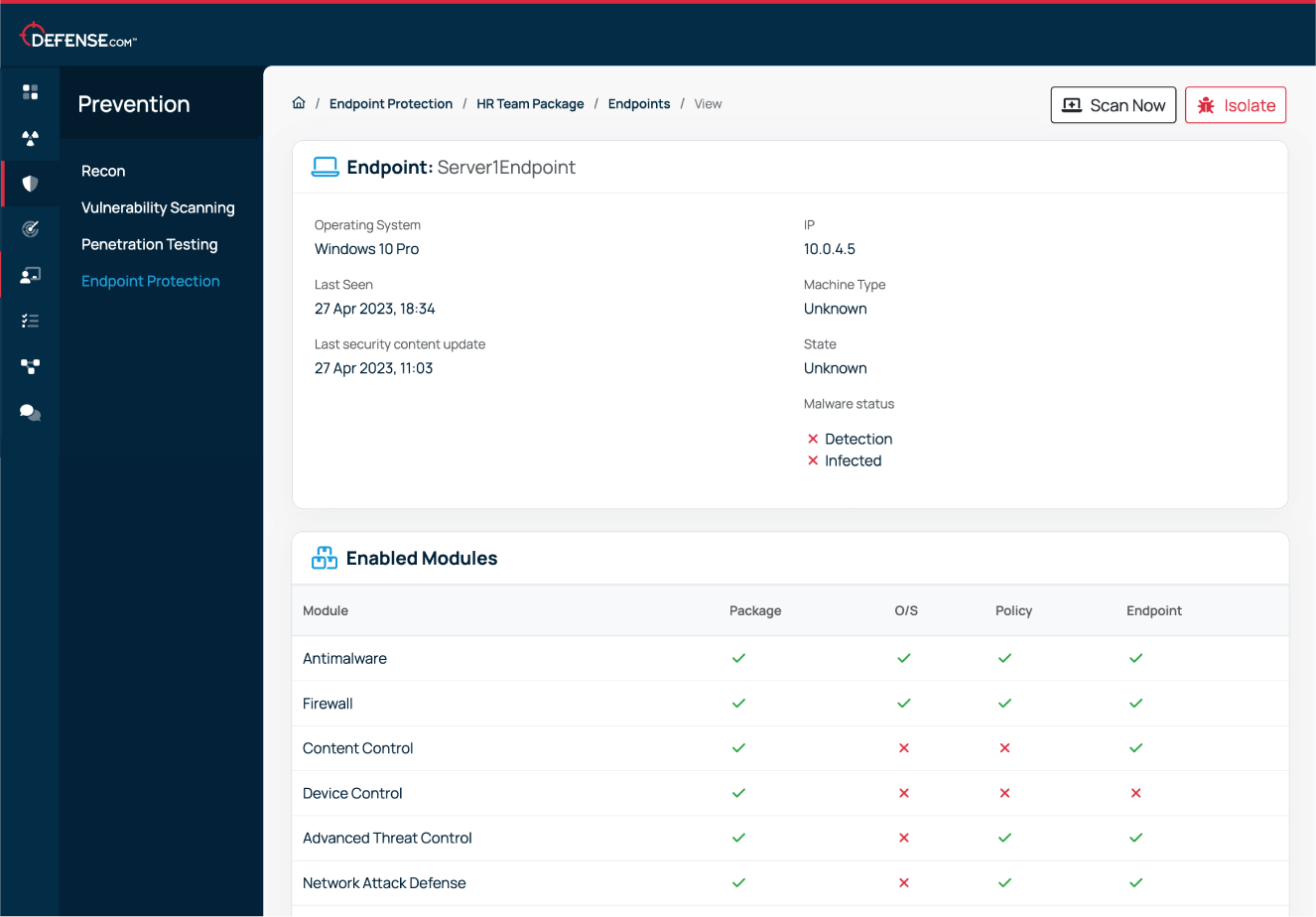
Create and deploy custom endpoint packages for users that require additional security controls, such as your finance and leadership teams.

Respond to indicators of compromise (IoCs) and stop attacks from spreading by isolating devices from your network. Get clear, step-by-step remediation advice to fix issues fast.
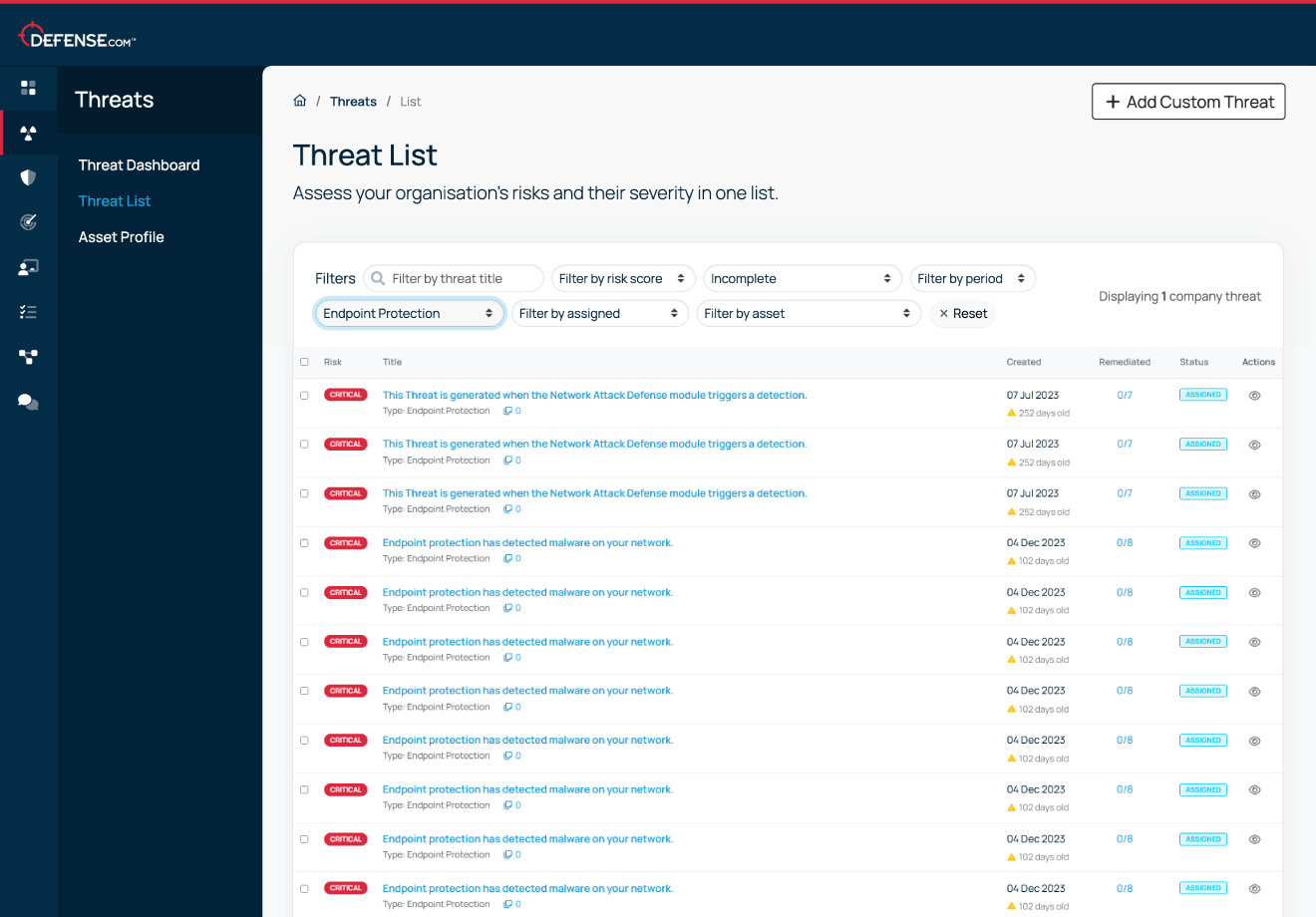
Get notified to new threats affecting your endpoints. Each threat is prioritised in order of criticality, so you can focus on the most important issues first.





We believe that good cyber security doesn’t have to be complicated. That’s why Defense.com provides you with the detection and response capabilities to effectively reduce your cyber risk.
By combining security tools that identify threats across your environment, Defense.com enables you to prioritise and manage cyber threats with ease. Remediation advice provided by experienced security analysts ensures threats are dealt with quickly and efficiently.

The Defense.com Endpoint Protection agent supports Windows workstations and servers, Linux workstations and servers, and MacOS workstations.
Our Endpoint Protection agent includes the following features as standard. Some features may not be available on all operating systems or devices:
The Defense.com Endpoint Protection agent is designed to replace your existing endpoint software product. To avoid any issues during operation and to ensure optimum performance, we would advise uninstalling your current endpoint solution before installing the Defense.com agent.
This process can be configured automatically if you are deploying Defense.com via Microsoft Intune. Check out this help guide for more information.
Defense.com Endpoint Protection can be deployed manually via installation links or automatically via an endpoint management service such as Microsoft Intune.
For more information, please refer to the following guides:
Get actionable cyber security advice and insights straight to your inbox.