
The importance of patch management
Read more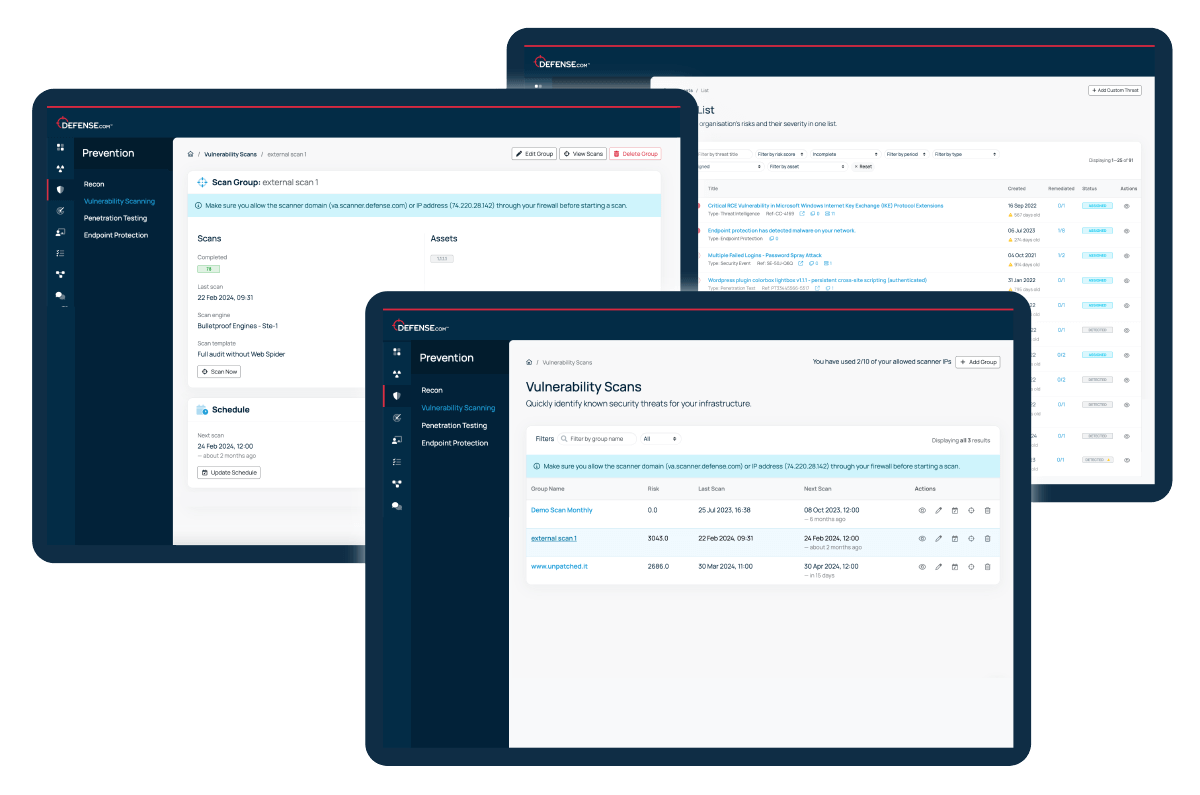
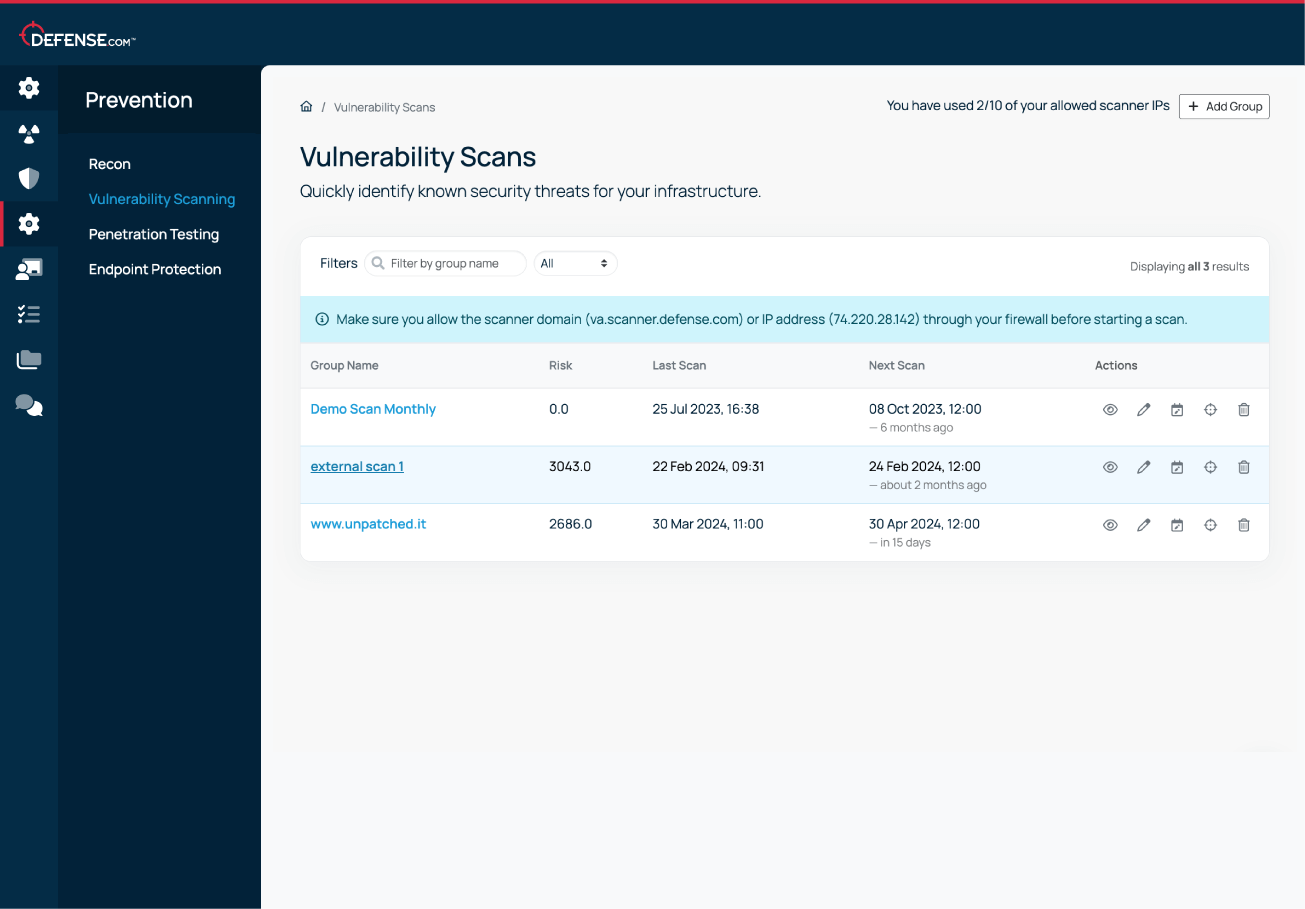
Find all known security weaknesses in your apps and infrastructure with the advanced Vulnerability Scanning engine in Defense.com.
Run internal or external scans to identify assets at risk of attack and get detailed remediation advice so you can patch issues quickly.
Try for free



























See how to set up and manage both internal and external vulnerability scans from a single dashboard. This quick walkthrough shows you how to schedule scans, manage assets, and turn findings into actionable fixes.
Our vulnerability scanning engine is always up-to-date with the latest vulnerabilities, so you’ll never miss a security flaw.
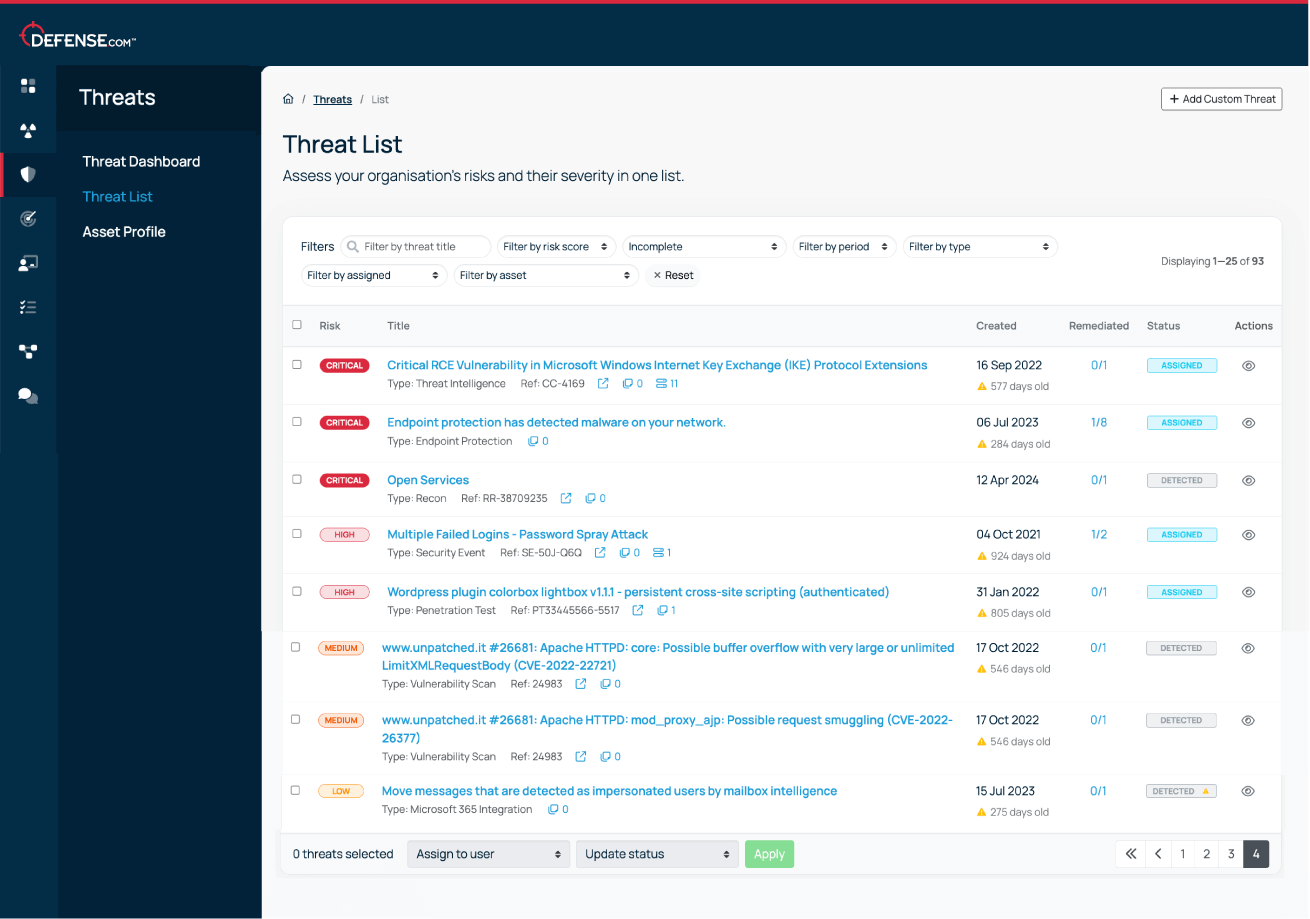
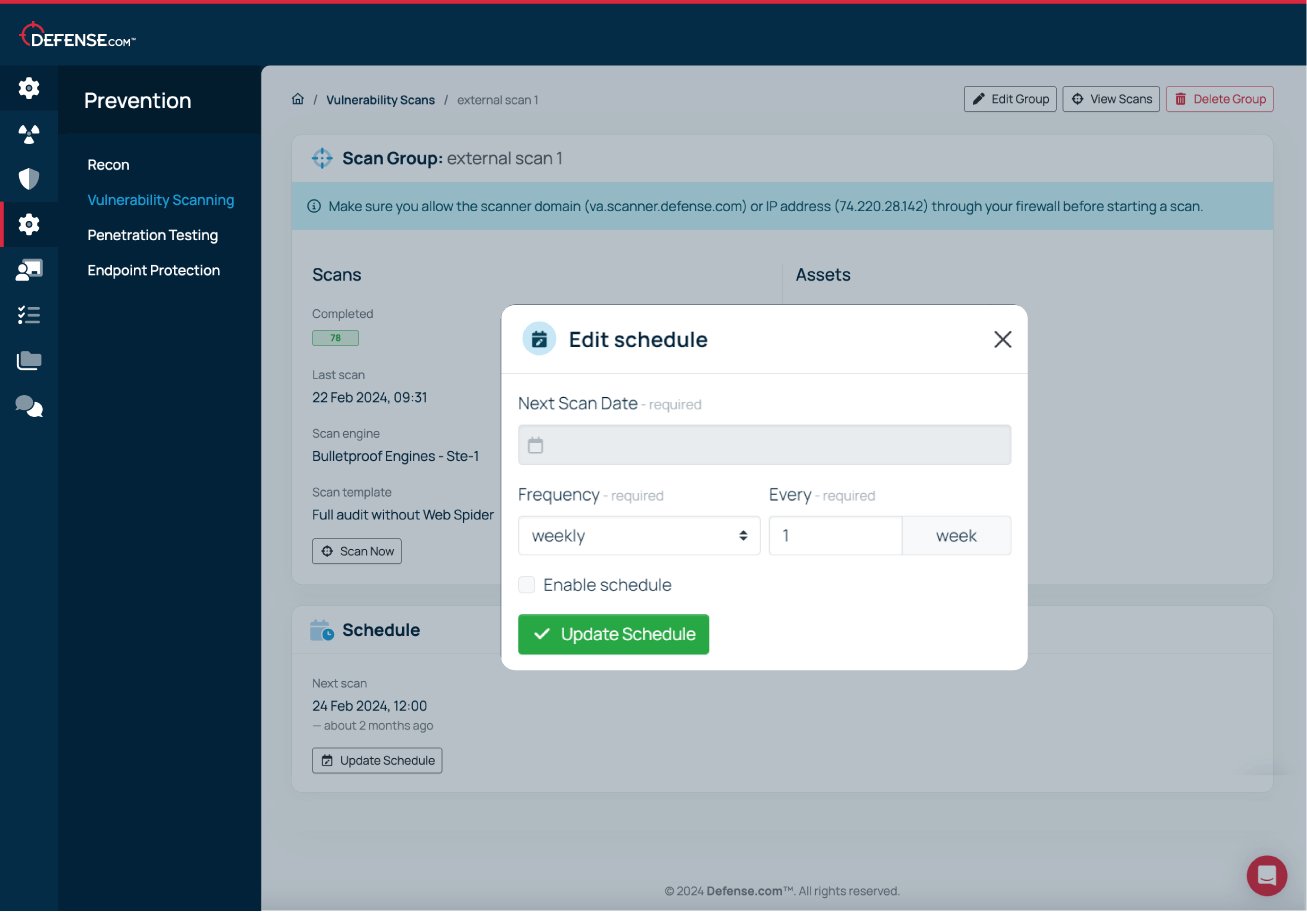
New exploits are discovered every day, so flexible scheduling makes running your custom VA scans a breeze. Scan on your own schedule and stay ahead of current and emerging threats.
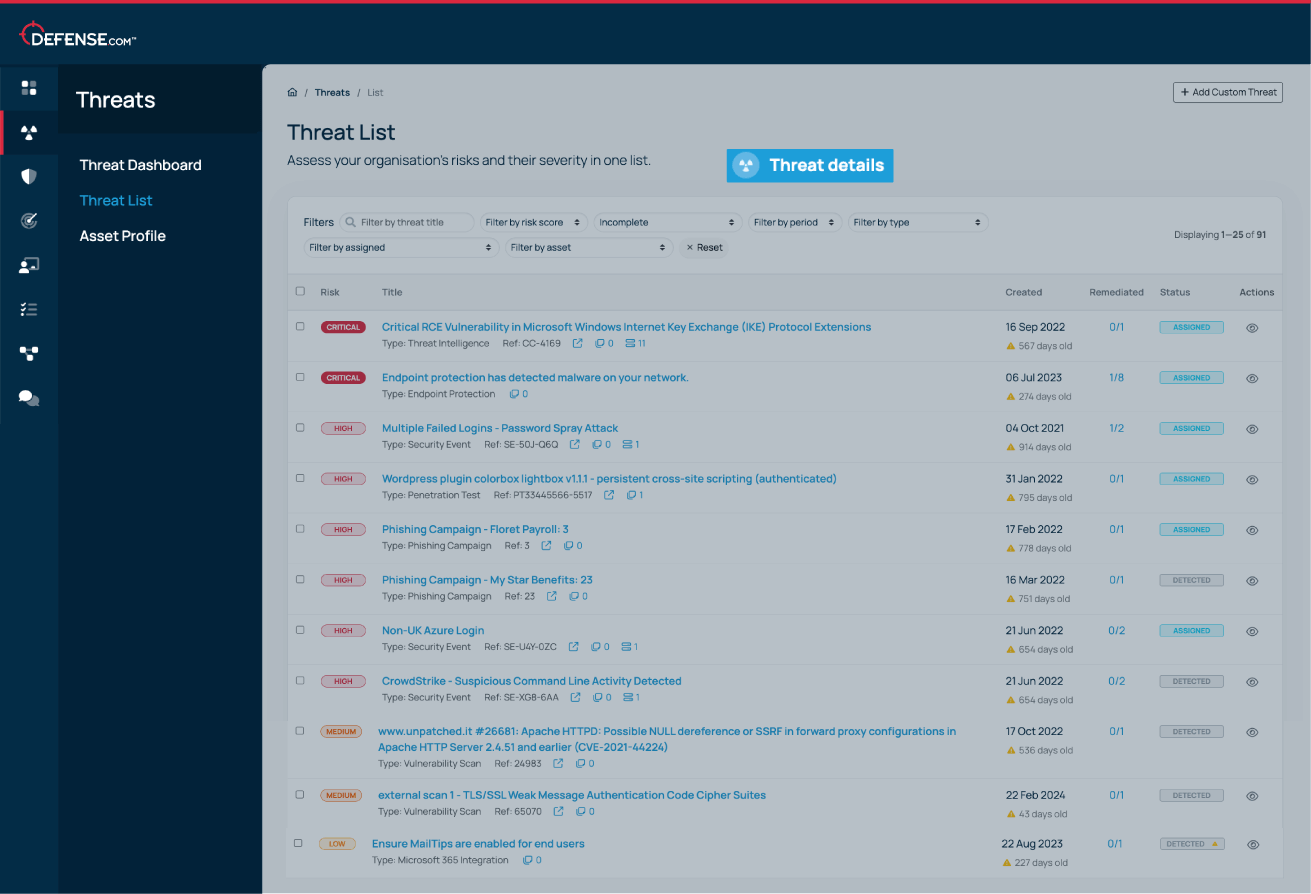
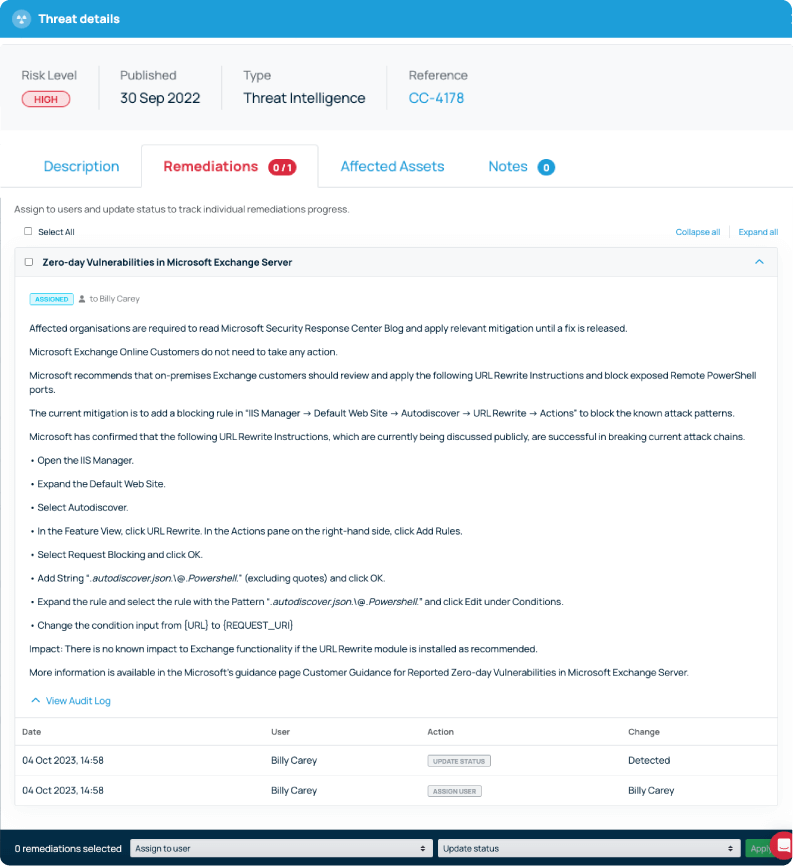
New vulnerabilities are automatically prioritised based on criticality, so you know where to focus your attention. You’ll also get detailed remediation advice to help you patch issues quickly.
Stay compliant with ISO 27001, the GDPR and PCI DSS with our easy-to-use vulnerability scanning tools.





We believe that good cyber security doesn’t have to be complicated. That’s why Defense.com provides you with the detection and response capabilities to effectively reduce your cyber risk.
By combining security tools that identify threats across your environment, Defense.com enables you to prioritise and manage cyber threats with ease. Remediation advice provided by experienced security analysts ensures threats are dealt with quickly and efficiently.

You can run as many vulnerability scans as you like for the domains/IPs you have registered in your scan group. It’s best practice to run a vulnerability scan every month, and you can use the scheduling tool in Defense.com to customise this to suit your needs.
The Defense.com Starter package includes 5 domains/IPs as standard, and you can add more at any time.
Yes, the Vulnerability Scanning engine in Defense.com can be used for both internal and external scans.
If any vulnerabilities are detected, they are automatically added to your Defense.com Threat List, which prioritises them in order of criticality and CVSS score. Each threat will contain detailed remediation advice to help you patch issues quickly before they are exploited.
You can see a full history of all completed scans, and you can also download a PDF report of each scan result if required.
Vulnerability scanning is an automated assessment that checks your apps and infrastructure for security vulnerabilities. It is commonly referred to as automated penetration testing, but it only detects known issues.
Penetration testing is more like a simulated, ethical hack, where a security professional uses their experience and insight to exploit flaws and misconfigurations in an attempt to compromise systems. This could include known and unknown vulnerabilities.
Penetration testing is usually conducted annually. Since new security flaws are found on a regular basis, scheduling vulnerability scans more frequently can help you keep on top of your security by making sure your systems are protected against the latest threats.
Get actionable cyber security advice and insights straight to your inbox.