
Log monitoring: A complete guide
Read more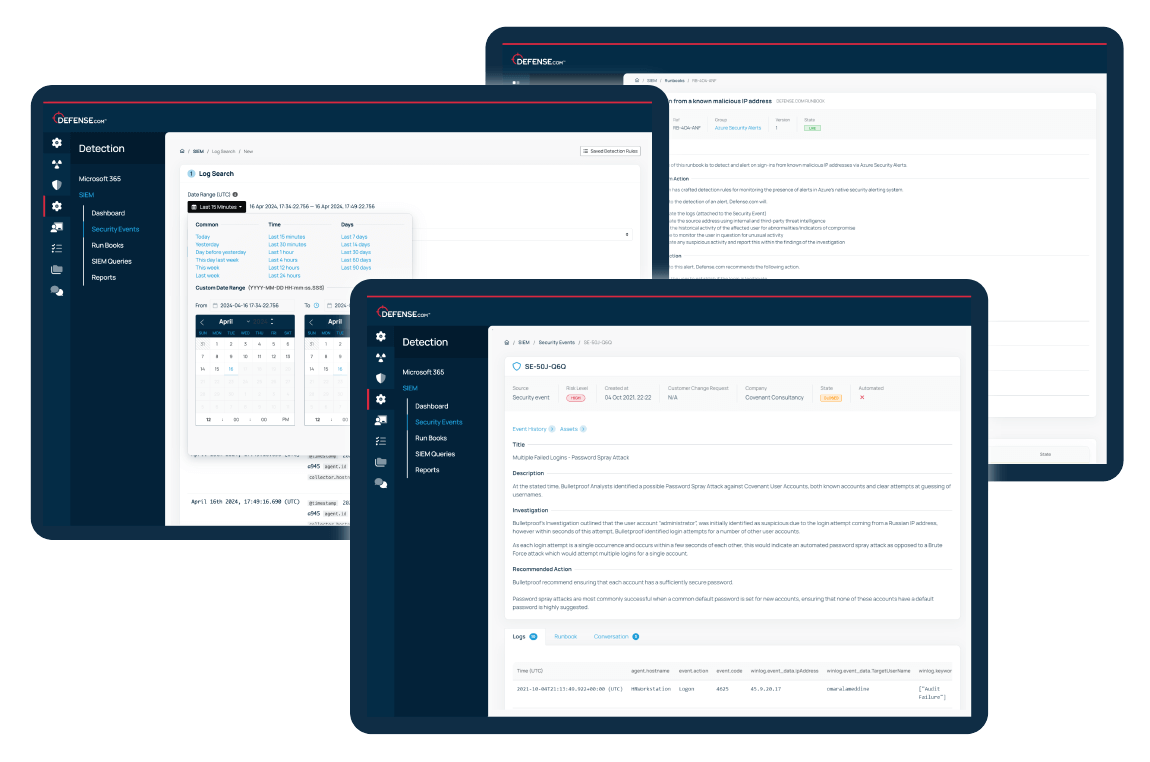
Defense.com helps you to monitor security logs and detect suspicious activity in your network with a cloud-native SIEM platform.
Our proprietary SIEM technology collects and parses logs from any source, helping you to identify threats, investigate incidents and prevent breaches.
Try for free



























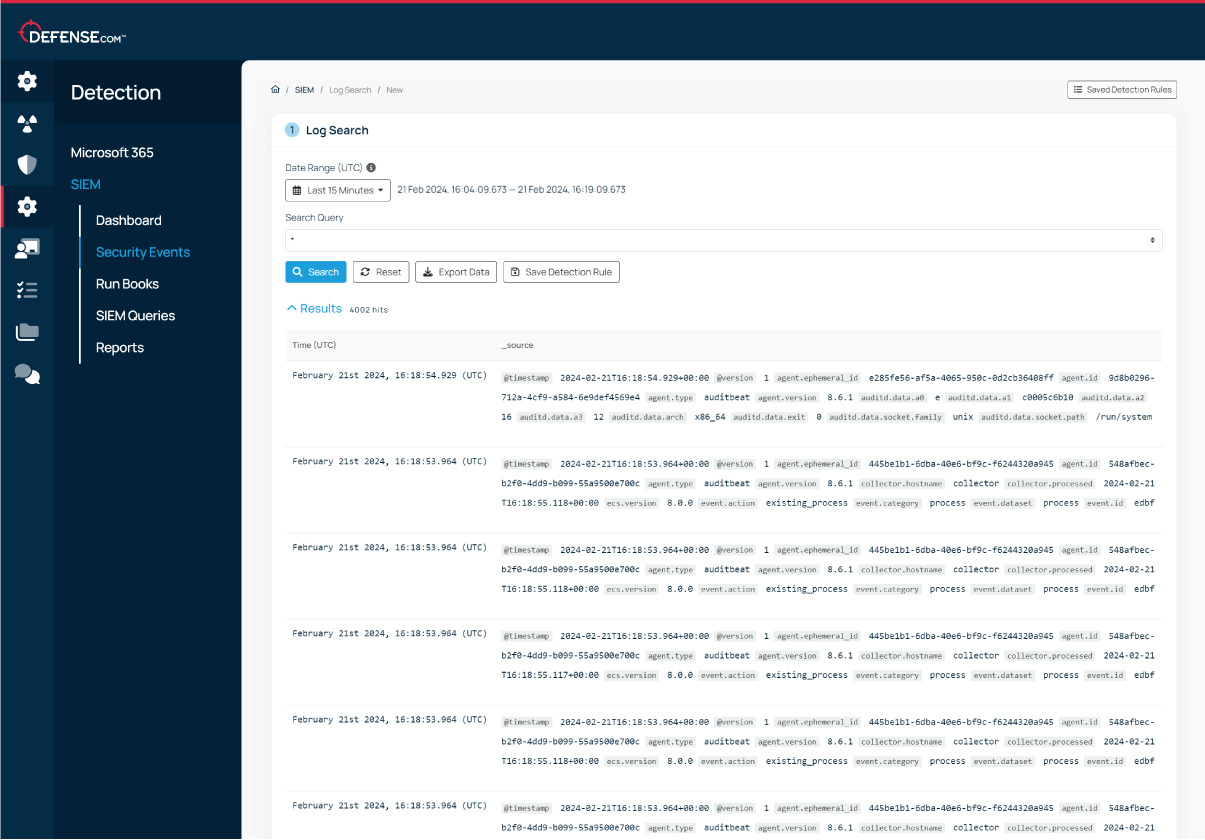
Ingest logs from any source that provides security value, so you can maintain complete visibility over your environment. Defense.com automatically parses and analyses your logs to detect any threats.

Build your own custom queries to quickly search up to 90 days of always-hot log data, plus get up to 365 days of archive log data storage as standard to meet your compliance needs.
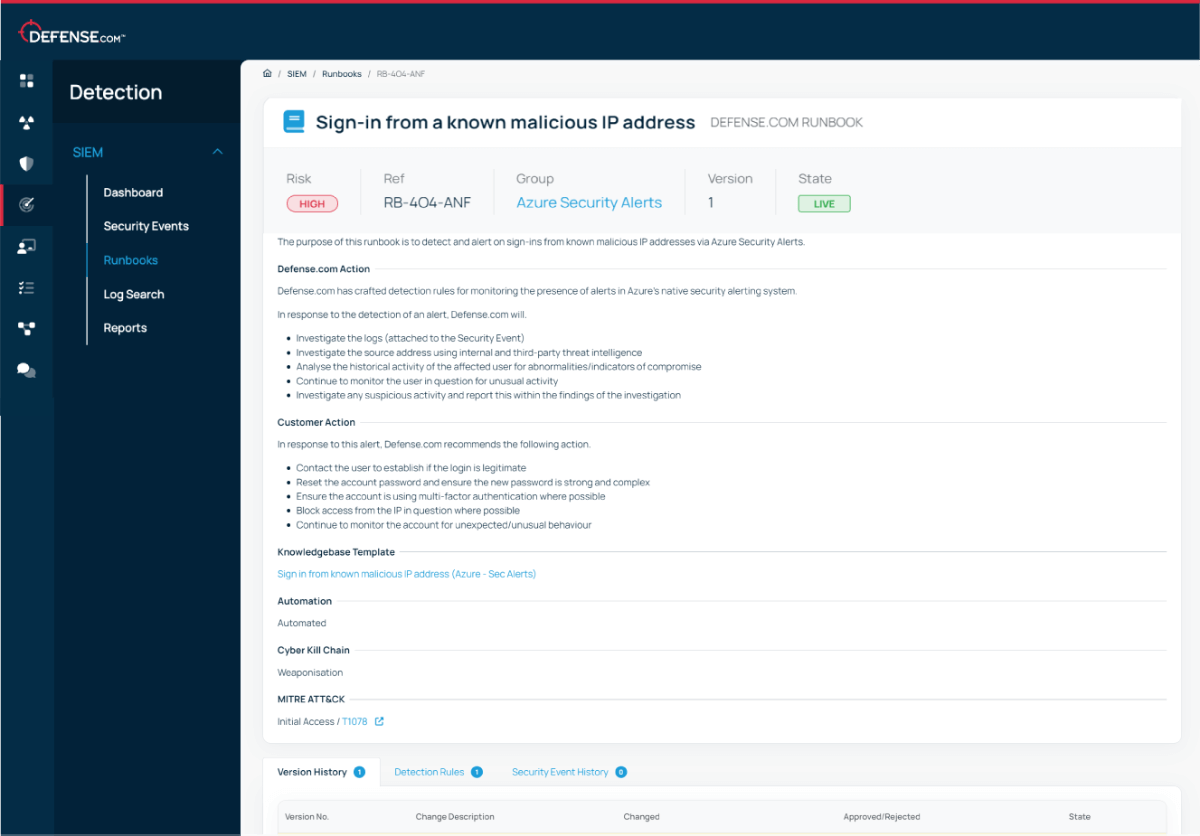
Our SIEM runbooks contain step-by-step advice to help you remediate threats. Each runbook is mapped to the MITRE ATT&CK, cyber kill chain and SANS frameworks to help you respond quickly and effectively.
Start seeing immediate value with our default runbooks or create your own to define custom response actions.
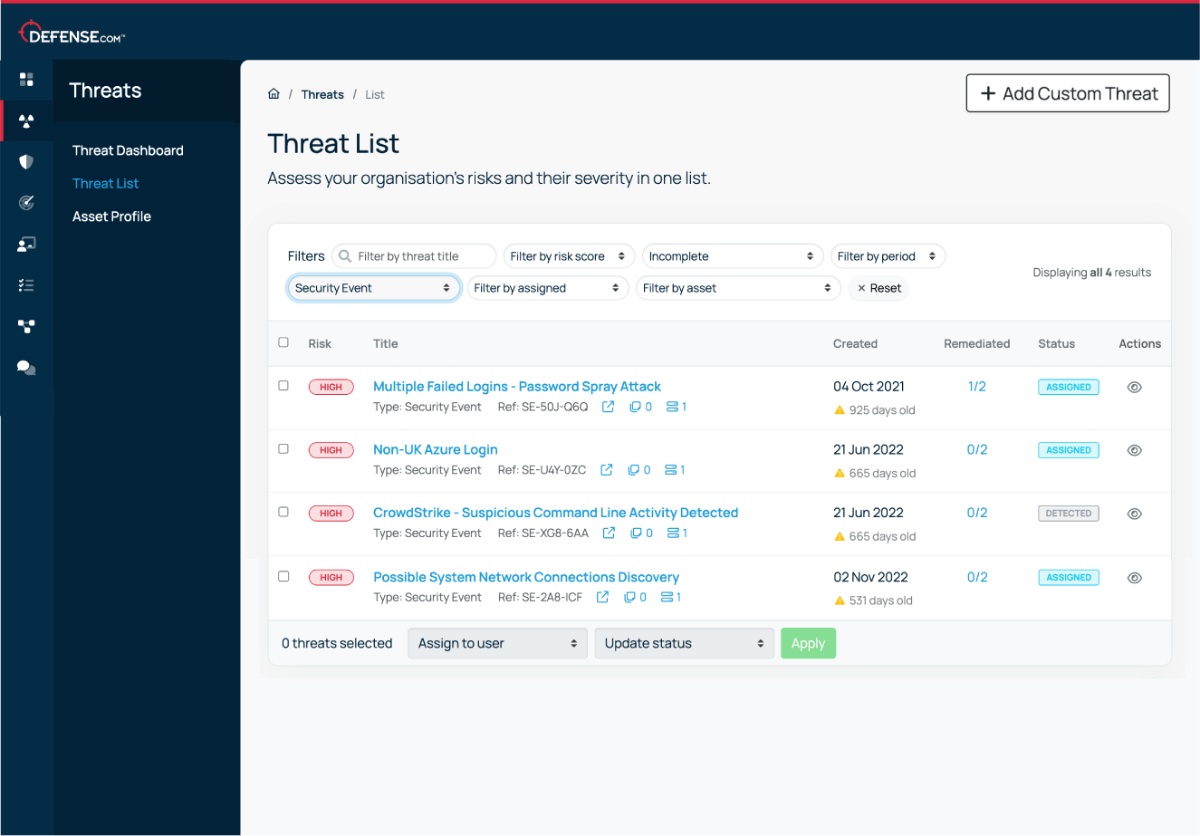
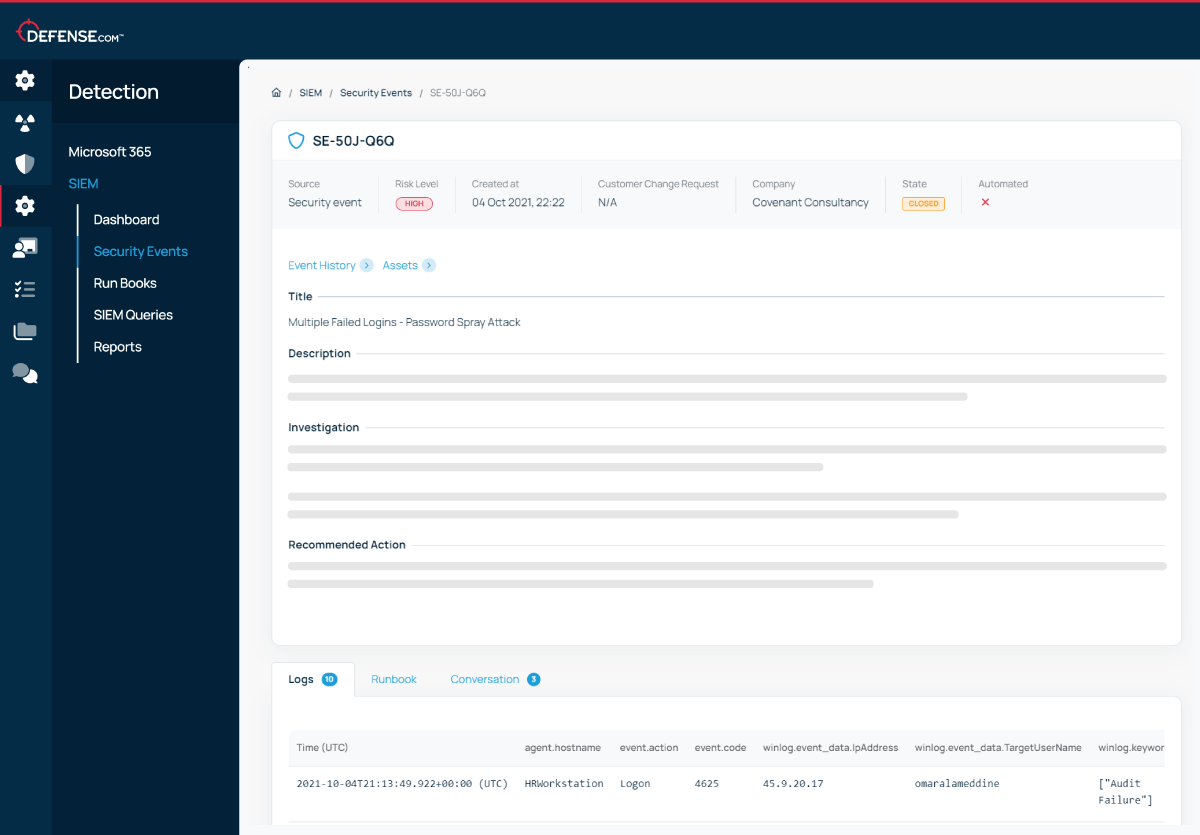
Know exactly where to focus your attention with automatic alert prioritisation. Each security event will contain a clear overview of the situation and the steps you need to take to remediate the threat.
See threats from all areas of your environment in a single dashboard. Automatic threat prioritisation enables you to focus on the most critical tasks first, saving you time and resources when investigating security events.








We believe that good cyber security doesn’t have to be complicated. That’s why Defense.com provides you with the detection and response capabilities to effectively reduce your cyber risk.
By combining security tools that identify threats across your environment, Defense.com enables you to prioritise and manage cyber threats with ease. Remediation advice provided by experienced security analysts ensures threats are dealt with quickly and efficiently.

For collecting logs within your network, a log collector using Ubuntu or Windows will need to be installed on a standalone virtual or physical machine inside your network.
Once this is complete, you will be provided with agents (Winlogbeat, Filebeat, etc.) which will need to be deployed to your client devices. The agents will send the logs from your client devices to the log collector. Once the logs have reached the collector(s), they will be sent to Defense.com for processing. Logs are encrypted when transferred via your client devices to the collector, as well as from the collector to Defense.com.
Since the Defense.com SIEM platform is SaaS-based, there is no need to build or maintain any further physical infrastructure in your environment.
For cloud platforms, it is preferable to collect logs via the vendor's API. Our Customer Success team will be on-hand to assist you with onboarding and ensuring that all of your logs are being ingested correctly.
Defense.com can receive logs from any source, system or vendor that provides security value, including:
Unlike other vendors on the market, with Defense.com there is no limit on the number of logs you send to us. Our pricing is based on the number of log sources, which means you don’t need to worry about log counts or daily ingestion rates.
As standard we provide up to 90 days of logs for immediate searching via your Defense.com account and up to 12 months offline. All logs are stored in a forensically-compliant manner. We can also cater for any particular requirements that your business has, such as the retention of logs for regulatory compliance purposes.
Get actionable cyber security advice and insights straight to your inbox.