
From risk to resilience: The secure by design advantage
Read more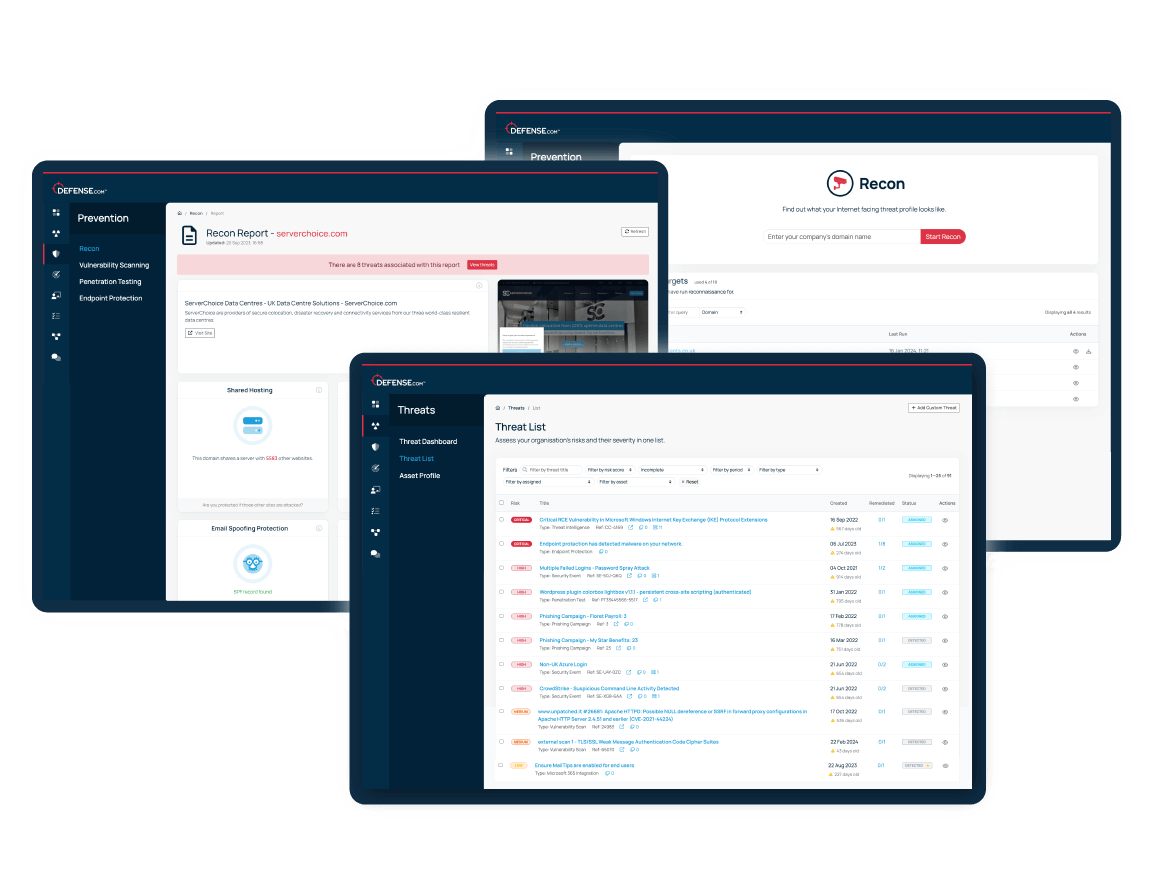
See your business through the eyes of a hacker:
Uncover any areas of your external attack surface that could become threats, so you can fix them before they are exploited.
Try for free



























See how quickly you can scan your domain and uncover hidden security risks in your external attack surface. This quick demo walks through the scanning process and shows how to turn insights into action with our threat management system.
Threat Recon uses a range of sources to detect potential external threats, including web traffic figures, subdomain detection, third party data risks and much more.
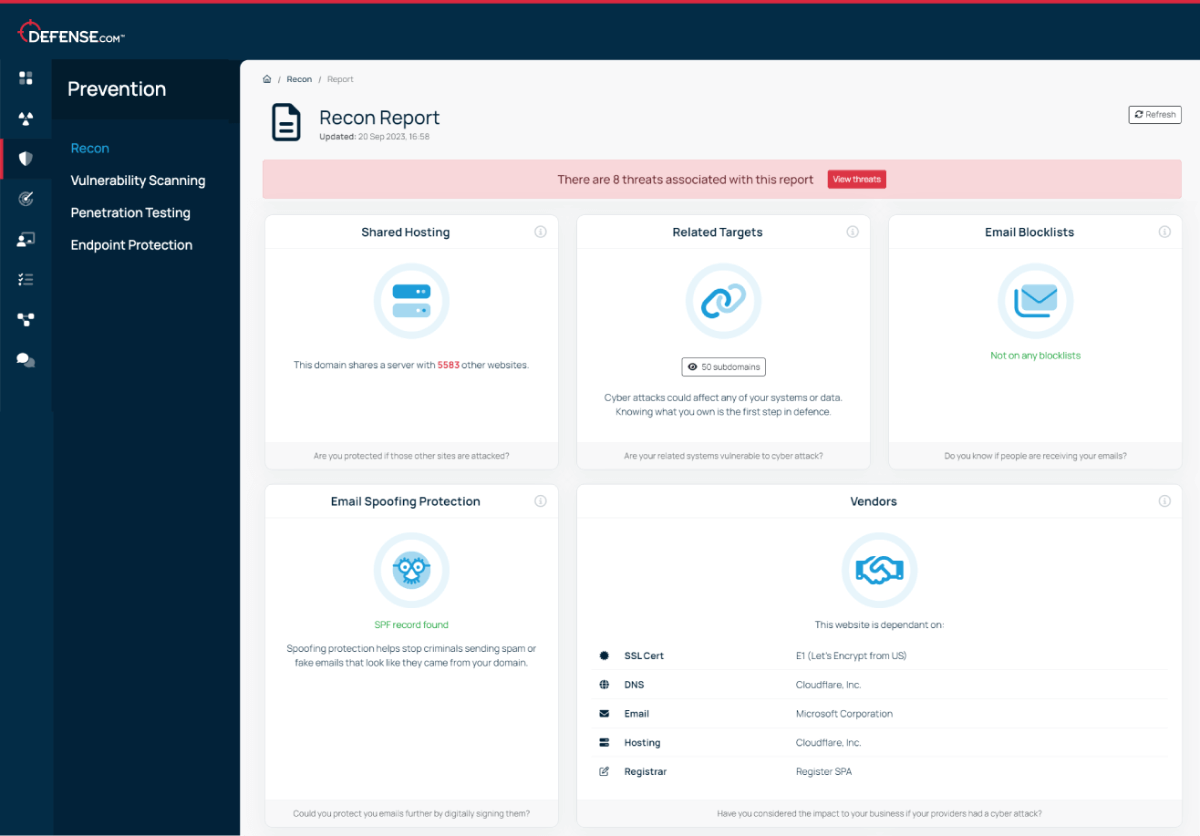
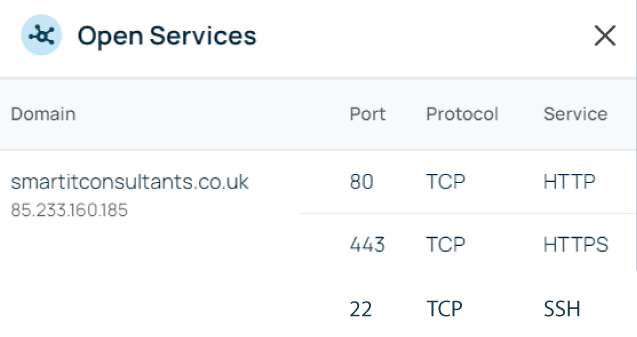
Threat Recon shows you which of your ports are publicly visible, so you can disable any unnecessary services and reduce the risk of them being exploited.
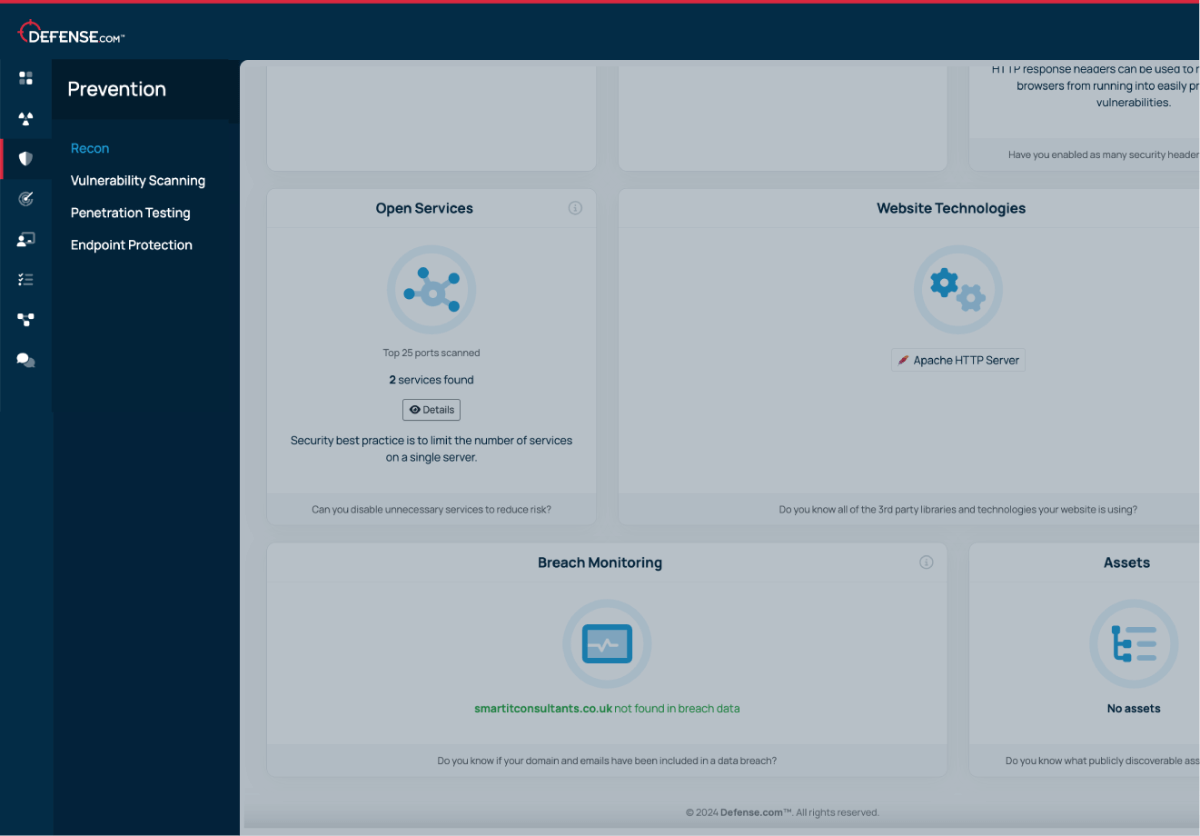
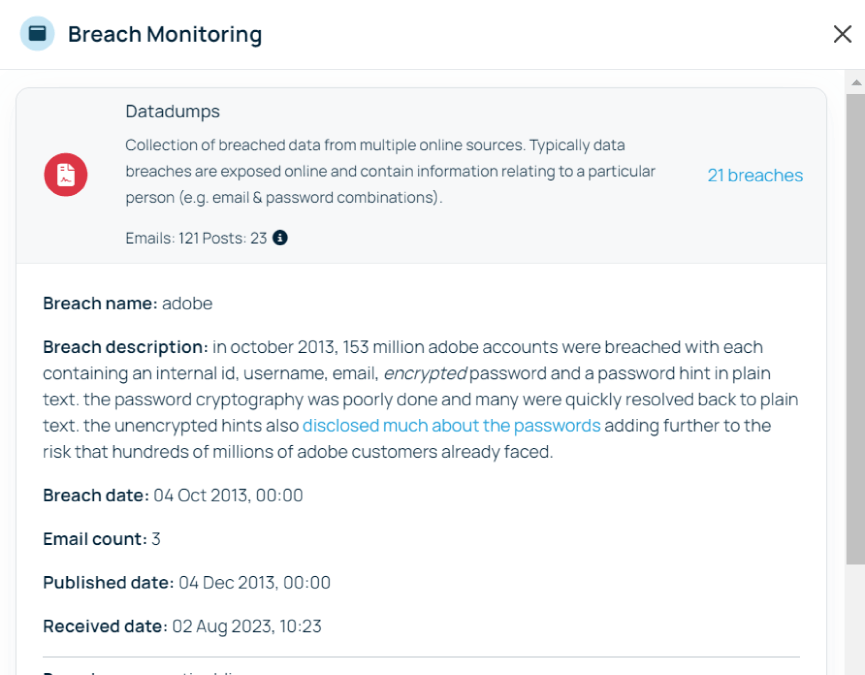
Find out if your domain and emails have been included in data breaches. Threat Recon safely scans locations across the surface web and dark web to alert you to any compromises.
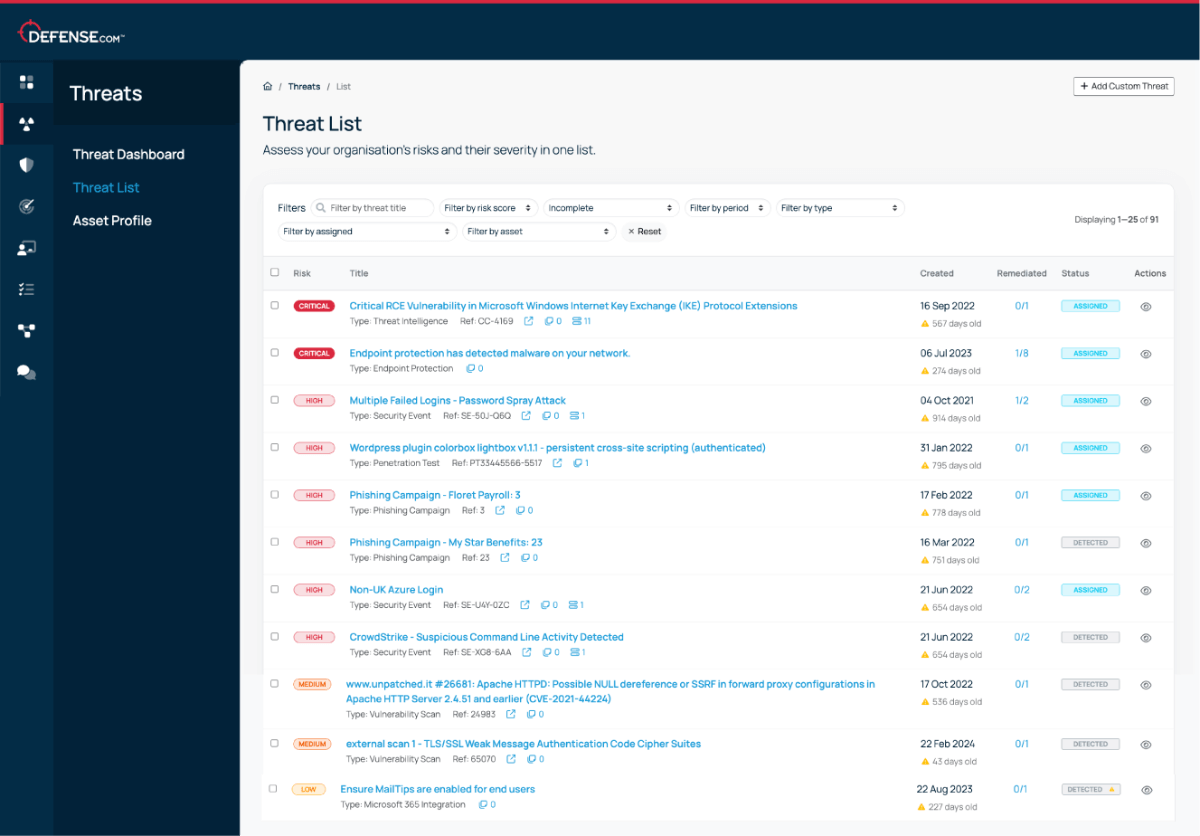
Threats are automatically prioritised in order of criticality, so you know exactly where to focus your time and attention.




We believe that good cyber security doesn’t have to be complicated. That’s why Defense.com provides you with the detection and response capabilities to effectively reduce your cyber risk.
By combining security tools that identify threats across your environment, Defense.com enables you to prioritise and manage cyber threats with ease. Remediation advice provided by experienced SOC analysts ensures threats are dealt with quickly and efficiently.

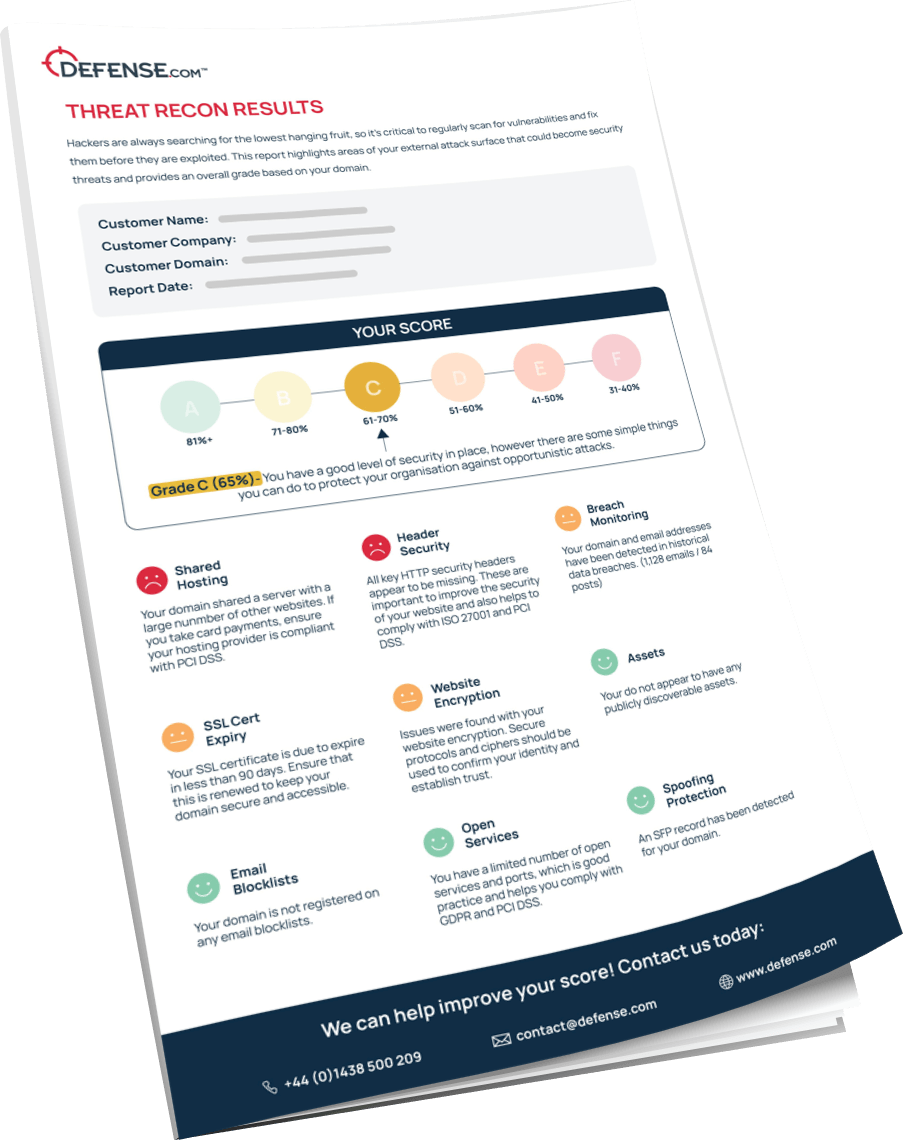
You can run a Threat Recon scan on your web domain as many times as you like. We’d recommend doing this on a regular basis to check for new threats from your external attack surface, particularly if your environment has changed.
Threat Recon scans your web domain and will provide the following data:
Yes, if your business has multiple domain names you can add these to Threat Recon and get a separate report for each domain. You’ll get a set number of Threat Recon domains as part of your Defense.com package, but you can contact us to add more at any time.
Get actionable cyber security advice and insights straight to your inbox.