
How to perform a cyber security risk assessment
Read more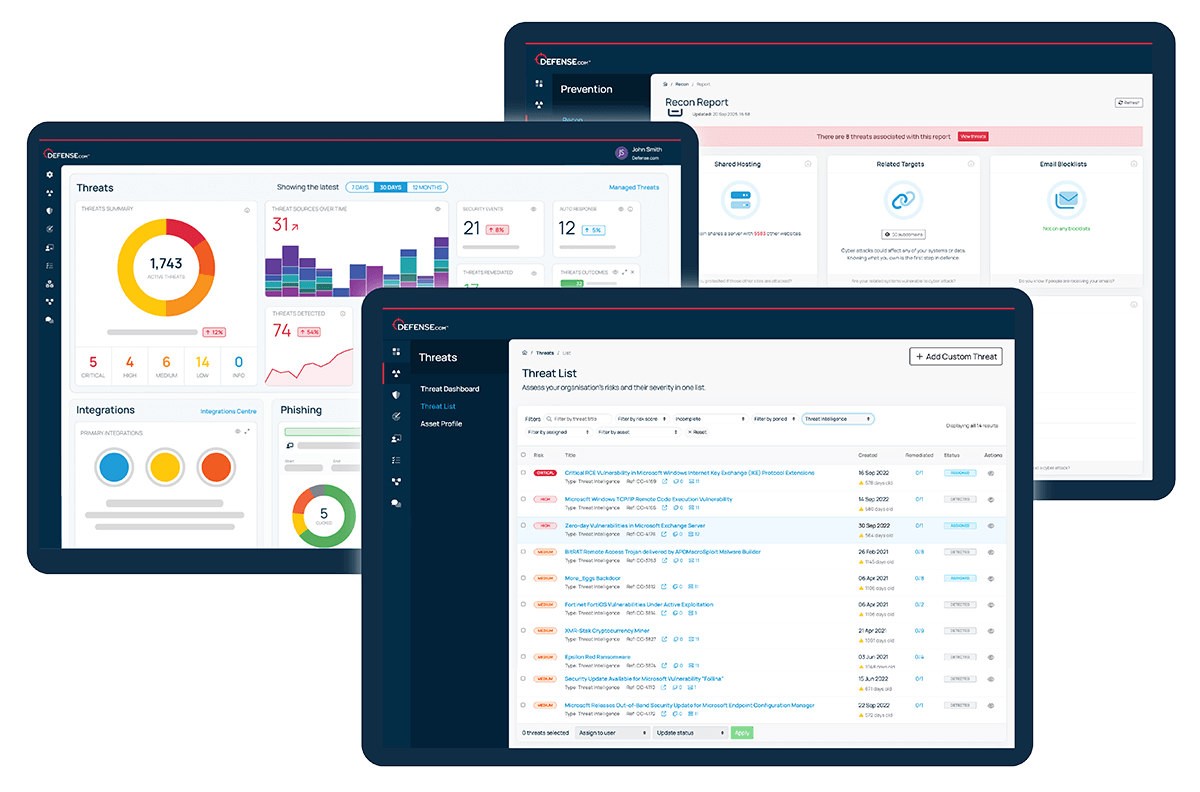
Stay up to date with new and emerging security vulnerabilities with the threat intelligence feeds in Defense.com.
Defense.com uses a variety of intelligence sources to keep you informed about the latest security weaknesses, with step-by-step remediation advice to help you patch them quickly.
Try for free





























Keep up to date with the latest vulnerabilities from industry sources such as MITRE CVEs, CISP, NHS Digital and a variety of open source feeds.
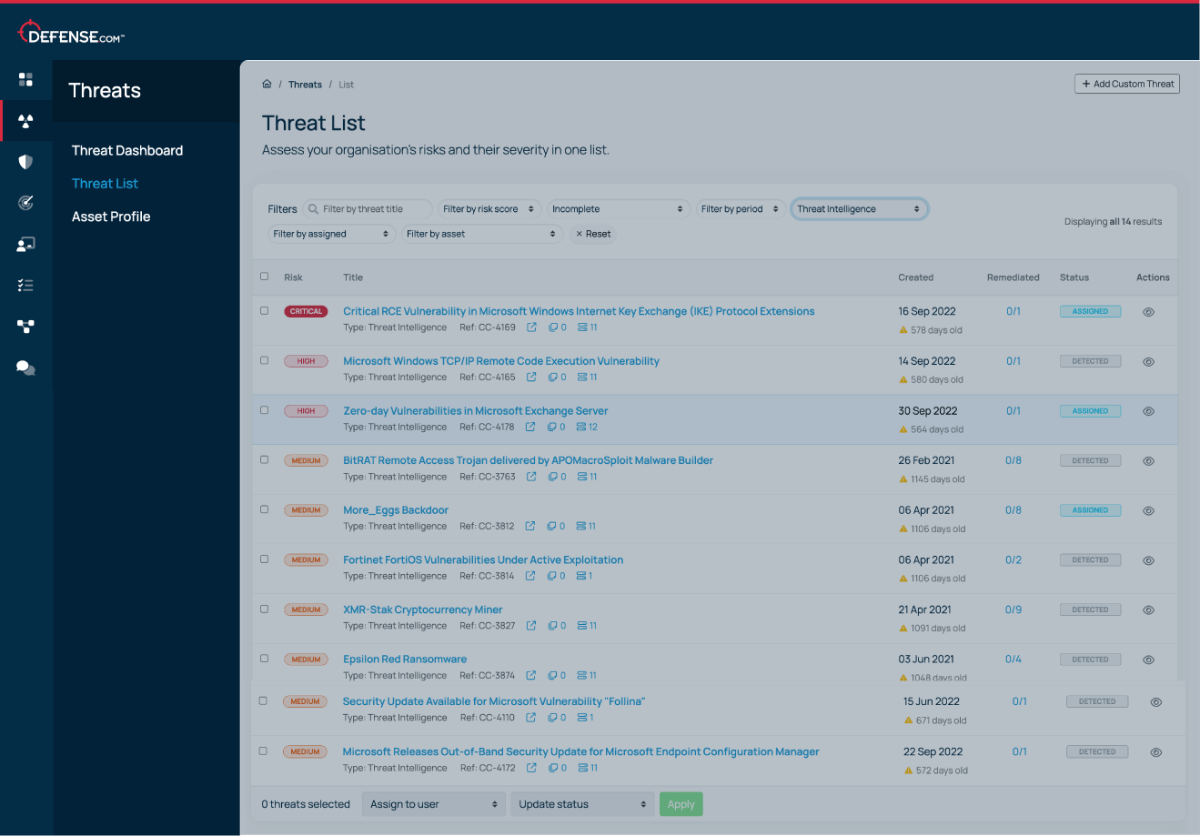
Defense.com automatically generates threat intelligence data based on your unique company profile, alerting you to new vulnerabilities that are relevant to your assets.
Find out if your domain and emails have been included in data breaches. Threat Recon safely scans locations across the surface web and dark web to alert you to any compromises.
Our team of SOC analysts use anonymised data from thousands of other Defense.com users to alert you to hidden and emerging threats.

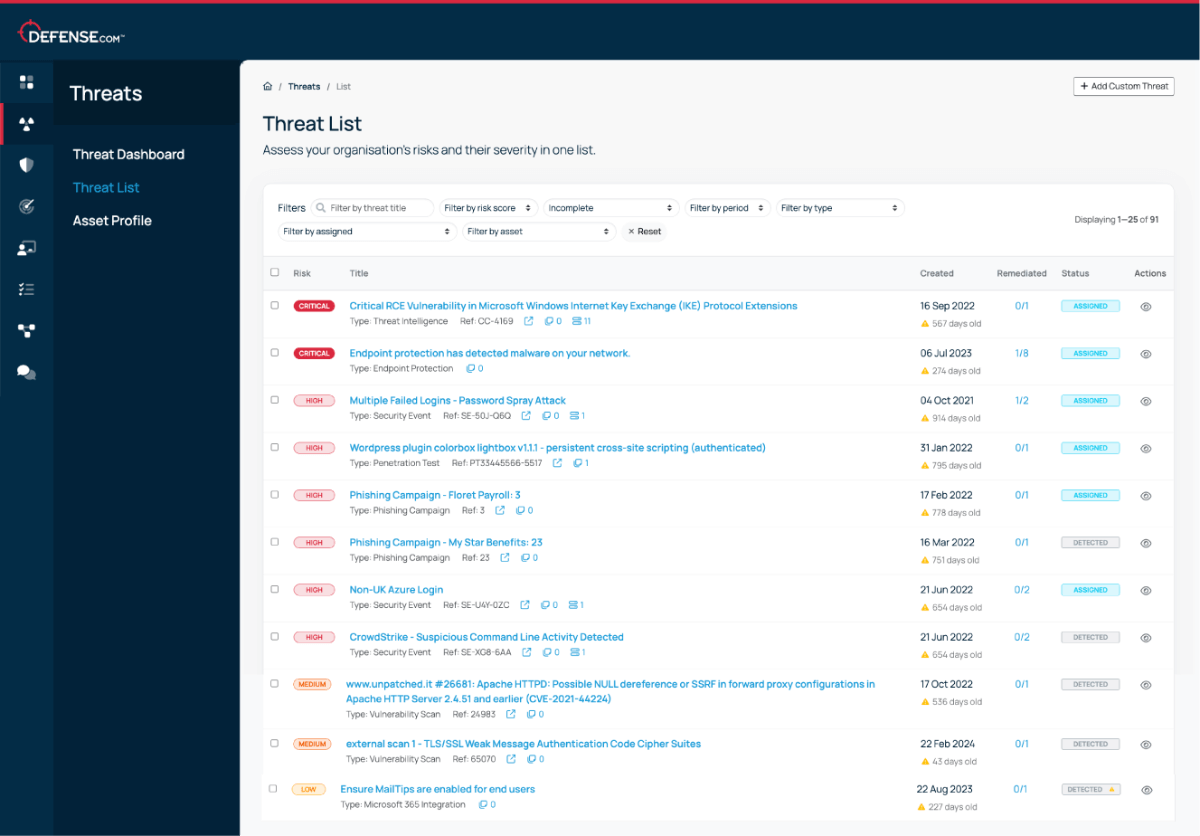
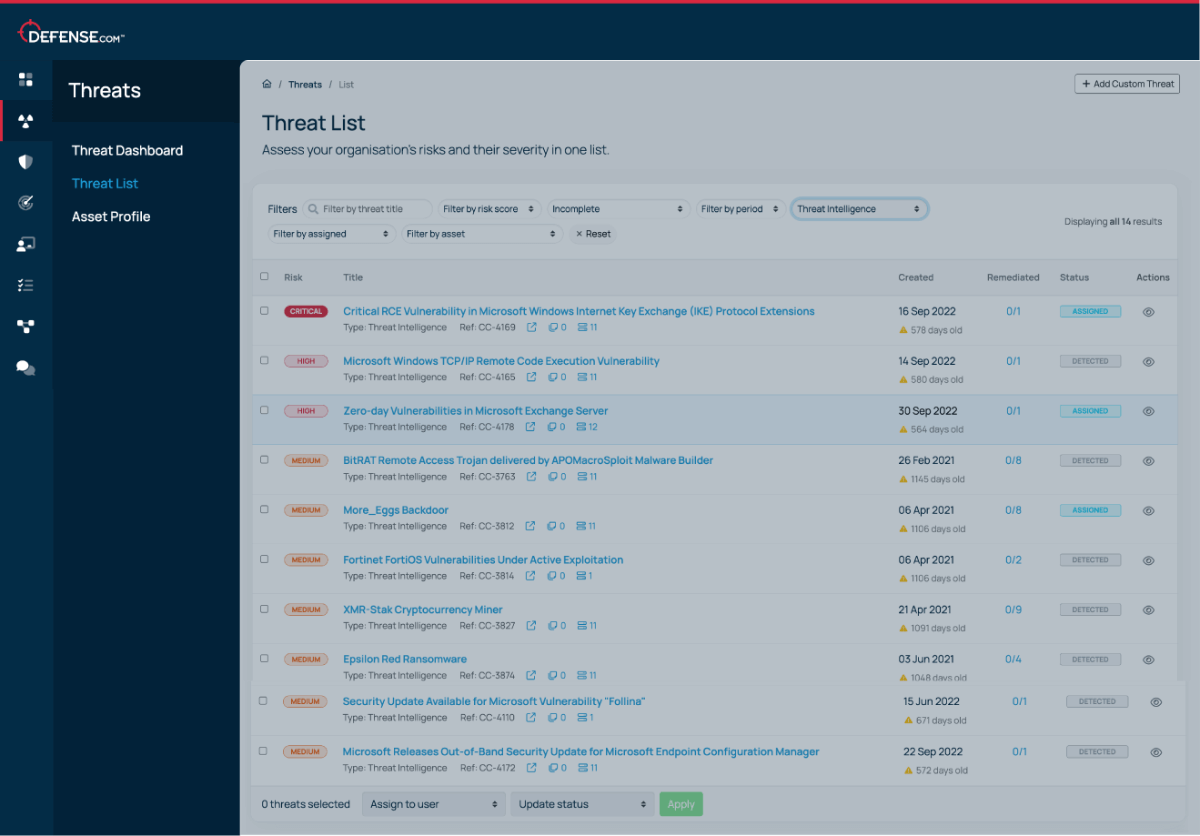
See threats from all areas of your environment in a single list. Automatic threat prioritisation enables you to focus on the most critical tasks first, saving you time and resources.





We believe that good cyber security doesn’t have to be complicated. That’s why Defense.com provides you with the detection and response capabilities to effectively reduce your cyber risk.
By combining security tools that identify threats across your environment, Defense.com enables you to prioritise and manage cyber threats with ease. Remediation advice provided by experienced security analysts ensures threats are dealt with quickly and efficiently.

Defense.com uses several threat intelligence sources to help you build a full picture of your threat landscape, including:
In addition to our general threat intelligence data, we can also include specific intel feeds that are aligned to your industry or sector. For example, we support a range of NHS trusts by providing data from the NHS Digital platform (formerly CareCERT) and threats specifically related to the healthcare sector.
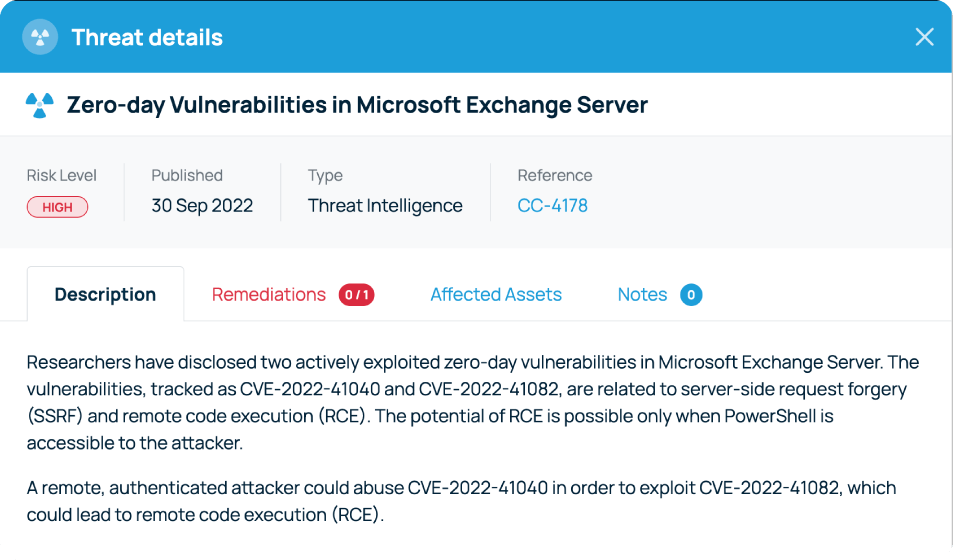
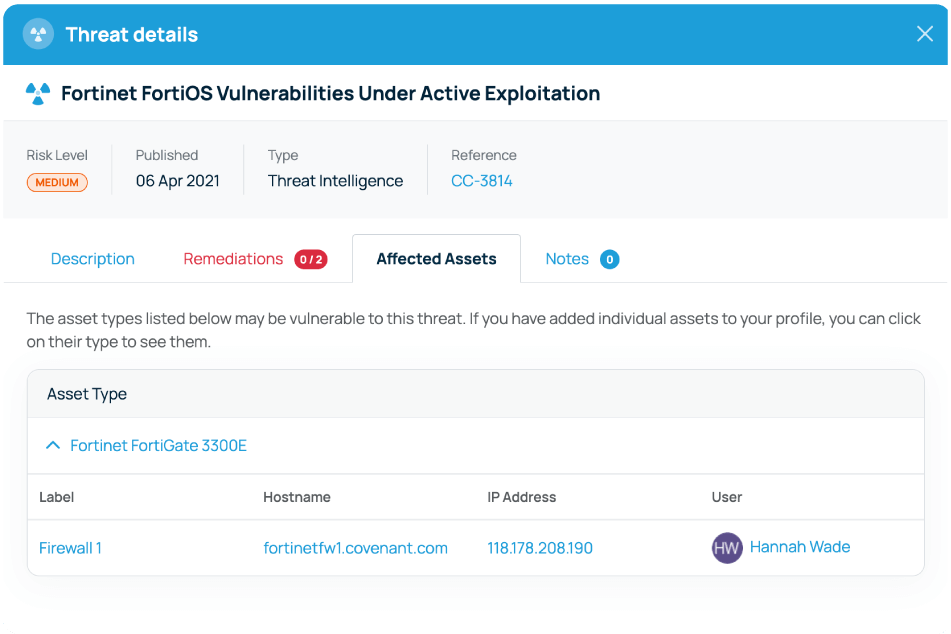
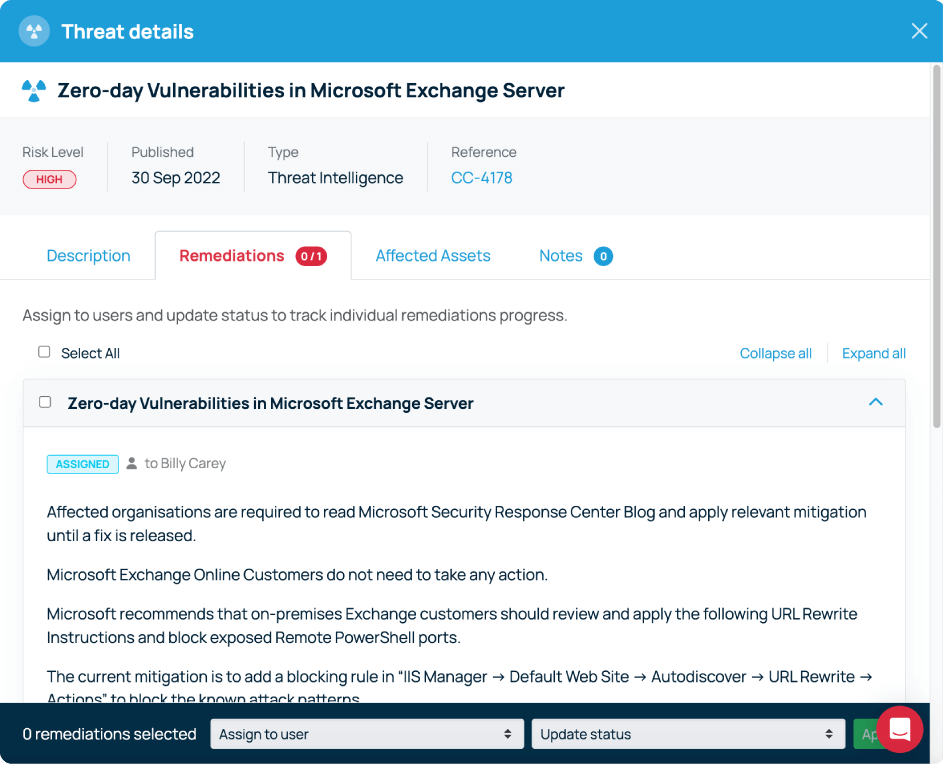
New threat intelligence data is automatically raised in your Defense.com Threat List and sorted in order of criticality. Each alert will contain a detailed description of the vulnerability, an overview of which assets are affected, and step-by-step remediation guidance.
Get actionable cyber security advice and insights straight to your inbox.