Competitive pricing
Our competitive penetration testing prices allow businesses to benefit from a certified penetration test.
Affordable penetration testing prices across app, network, infrastructure, cloud and much more.



Our competitive penetration testing prices allow businesses to benefit from a certified penetration test.
Track your report findings, prioritize threats and access remediation advice within the Defense.com™ platform.
Our penetration testers are certified by globally recognized bodies such as CREST and OSCP.
Protect your business all year round with 12 months of free vulnerability scans as part of your pen test package.










We pride ourselves on building and developing the best cyber talent to ensure our service is as evolutionary as the threat landscape. Our team of 30+ penetration testers are qualified against the leading industry standards and have years of experience delivering all types of penetration tests.
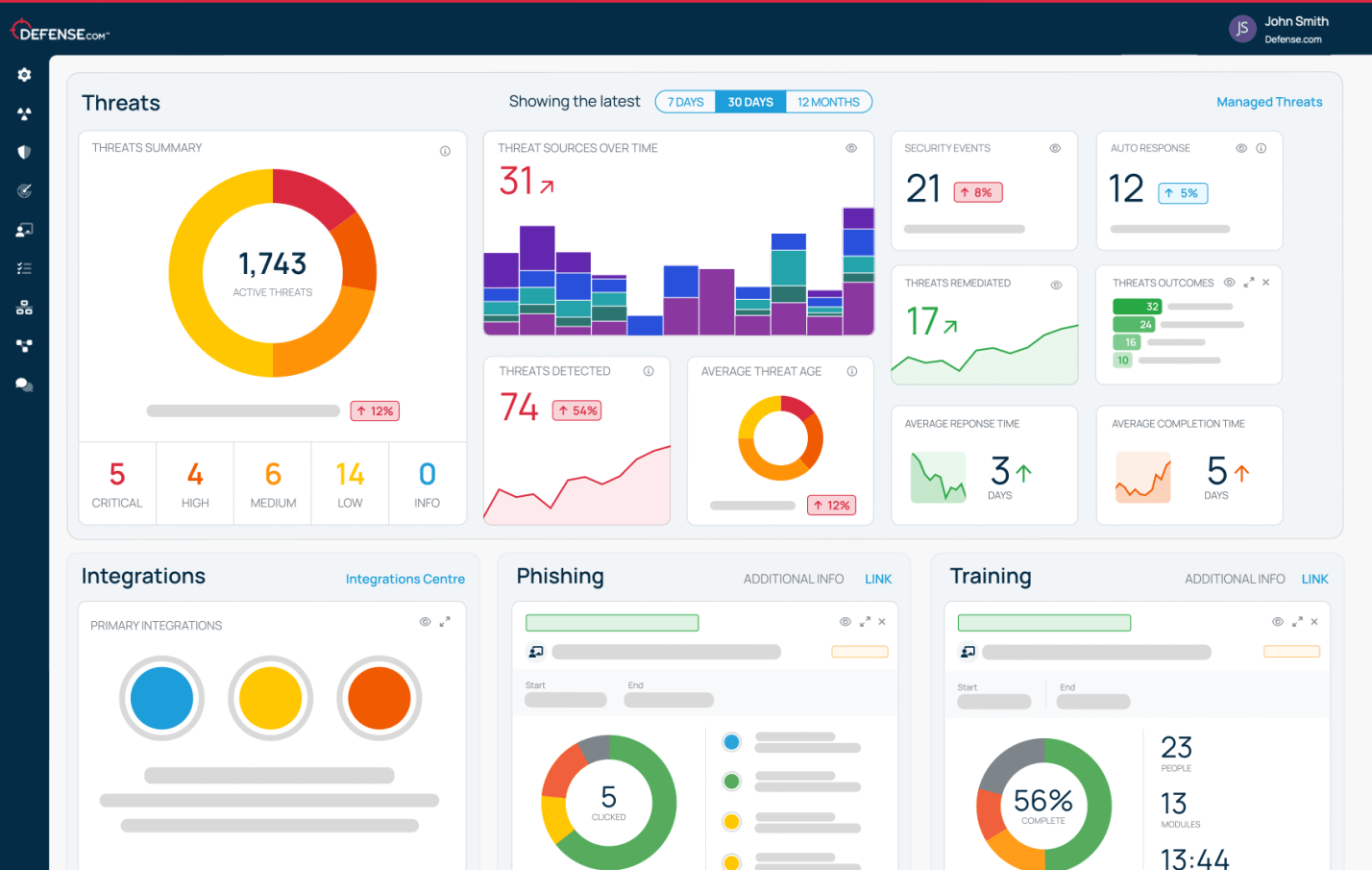
After your penetration test, your report findings will be hosted in your secure Defense.com™ platform. Each vulnerability found during the test will be detailed along with actionable remediation advice.
In addition to your PDF report, each vulnerability highlighted during the test will be added to your Threat Dashboard so you can quickly identify, prioritize and remediate the threats affecting your business.
Get a quoteMost penetration testing follows a 6-step lifecycle:




If you’re interested in learning more about how we can provide your business with an affordable penetration test, get a free, no obligation pen test quote today by submitting your requirements via the form below.
Penetration or pen testing, assesses your IT infrastructure security by methodically testing your systems and applications. Pen tests are carried out by skilled ethical hackers, called penetration testers, to find weaknesses and misconfigurations in your cybersecurity that could put your business at risk.
Penetration testing enables you to quickly find your security flaws, giving you the chance to fix them before a hacker exploits them. Penetration testing is highly beneficial to businesses of all sizes:
Regular penetration testing is a fundamental part of running a modern business. Cyberattacks increase steadily year-on-year across all markets and sectors, making pen testing a core consideration for businesses of all sizes.
In addition to keeping safe from cyber criminals, pen testing can help to increase customer confidence in your services. Regular penetration testing from a reputable provider such as Defense.com™ demonstrates that you take security seriously, which will prove to your existing and prospective customers that you can be trusted with their data.
There are many different types of penetration tests available. The scope of your test will depend on exactly what systems or applications you are looking to check. Here are some common types:
Infrastructure pen testing, also known as network pen testing, focuses on the hardware, firmware, and operating systems in your IT estate. This includes things like servers, network devices, and virtualized environments.
Application penetration tests focus on applications that are hosted on the underlying infrastructure, rather than the infrastructure itself. This could be web apps and APIs, or it could be mobile apps, such as iOS and Android penetration testing.
Cloud penetration testing audits the security of your cloud-based infrastructure, applications and services. AWS, Azure and GCP-hosted systems are the most commonly tested.
Internal infrastructure or authenticated application tests simulate the damage a malicious attacker could do if they were to breach your network perimeter or phish login credentials for an application. It’s a much more involved test, and also models the impact of a rogue employee or other insider threat.
External/unauthenticatedExternal infrastructure or unauthenticated application tests explore what damage a malicious hacker could achieve without privileged access. It’s a quicker test that models the more common ‘opportunistic’ type threat actor.
A Defense.com™ penetration testing engagement is split into several distinct stages:
This is where the scope is discussed and defined, and the ultimate goals of the pen test are analyzed and set. This stage will determine the types of testing activities and is essential for a professional and productive test outcome.
Having a good report is the key to getting good value from a penetration test engagement. Defense.com™ reports are split into Executive Summary and Technical Breakdown sections, and it includes crucial remediation advice.
The detail in pen test reports should include:
It’s a good idea to seek a sample report before engaging a pen test provider – this way you’ll know what you can expect to receive. If a report is full of jargon and difficult to decipher, its use to you is limited. Defense.com™ follows best–practice standards for undertaking a pen test, including OWASP and PTES.
When defining a penetration test, it is important to define how much information is disclosed up-front, also known as the box color:
A black box test is where almost nothing is known about the target environment ahead of the test. Whilst this positions the tester in a similar position to a real-world hacker, it means precious test time is wasted on simple discovery tasks.
A white box test is where everything about the environment, possibly even the source code, is known by the pen tester ahead of the test. Whilst this has the potential to make for a very thorough test, it’s not reflective of a real-world hack, and can cause the scope to become diluted.
There’s also a third option; as the name implies, a gray box test is a mix of white and black box tests, where the pen tester has limited information about the target environment. This is a ‘best-of-both-worlds’ approach and often leads to tests with the best – and most cost effective – outcomes.
Get actionable cyber security advice and insights straight to your inbox.