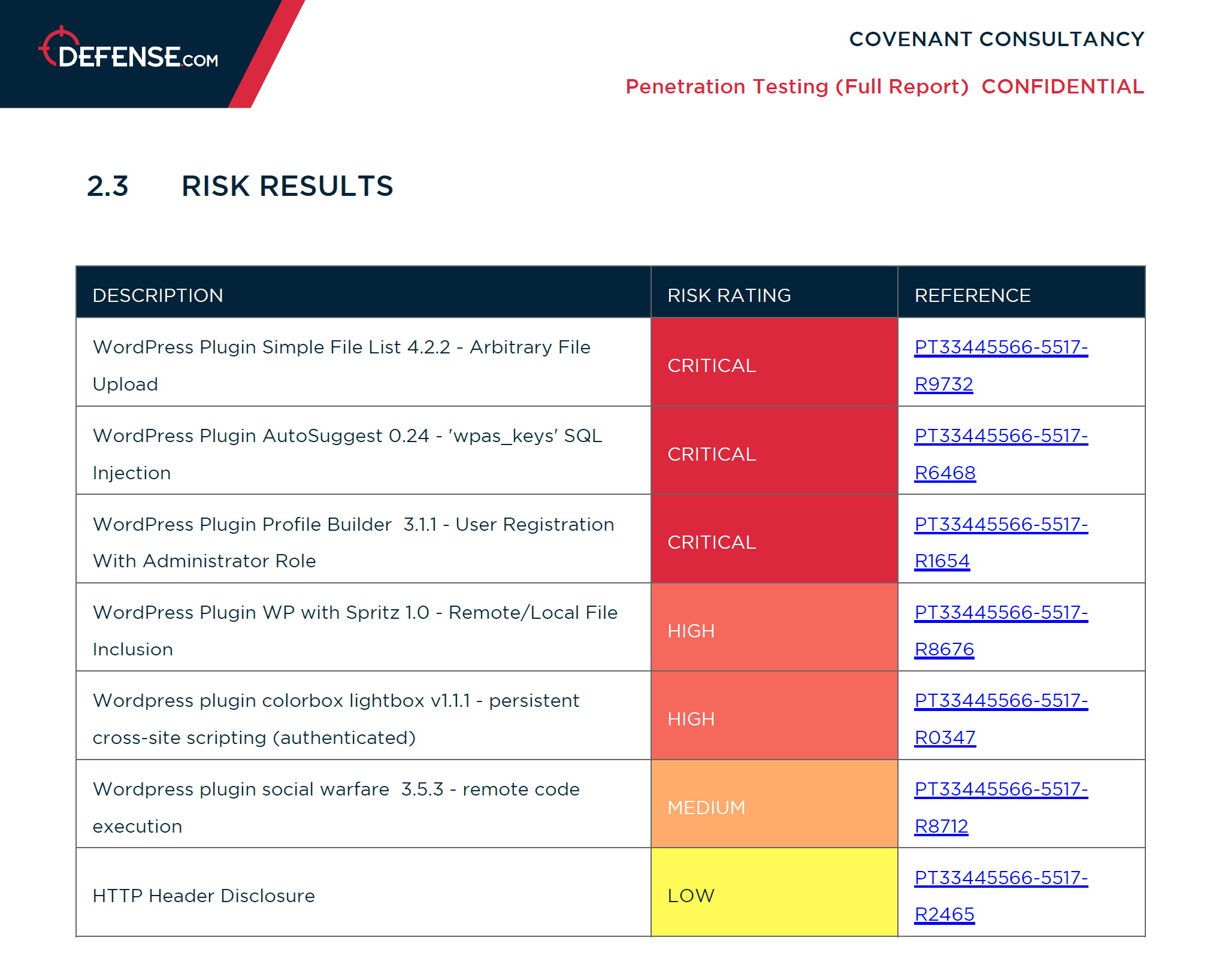
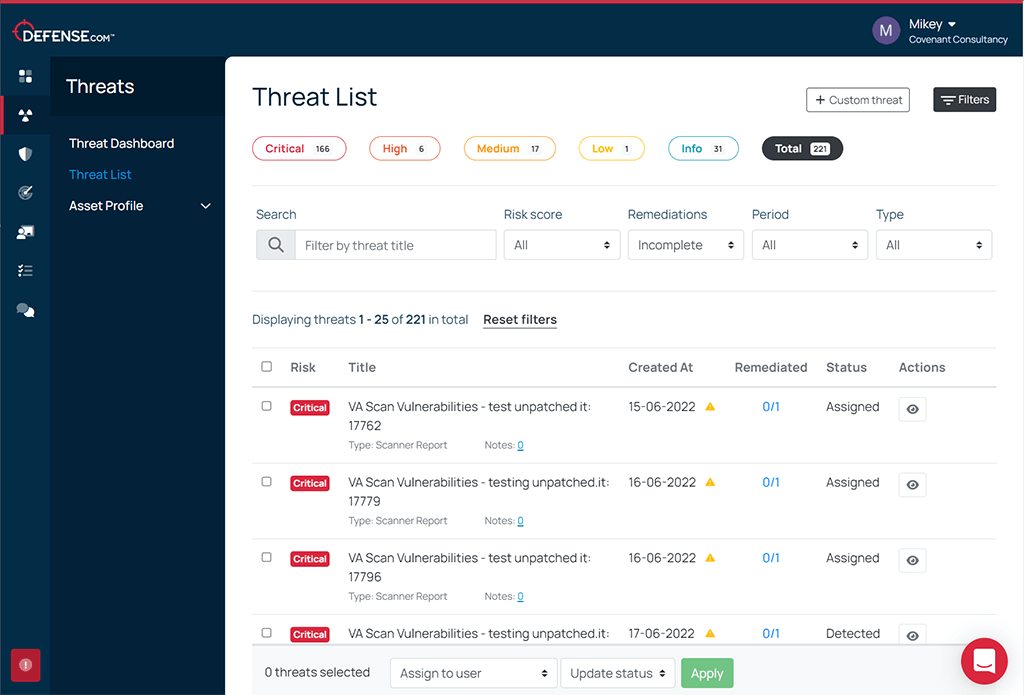
Authenticated tests
Analyze the security of your web app from a user perspective. Auditing the admin portal of your web application will reveal vulnerabilities including SQL injection, session fixation, privilege escalation and cross-site request forgery (CSRF).