70% of mobile app vulnerabilities are low effort to fix.
20% of these have a high likelihood of being exploited.
Identify mobile app vulnerabilities
Mobile application penetration testing assesses apps built for Android, iOS and other operating systems against common vulnerabilities and exploits.
Mobile penetration testing helps you understand the risks of your mobile application with minimal disruption to your business. Our testers will help you to:
- Uncover vulnerabilities and poor security strategies
- Identify any coding issues that could be exploited or reverse-engineered
- Expose insecure authentication, storage systems or data processing in your mobile app
- Help improve security throughout your software development lifecycle
Your certified penetration tester will provide a full report with their findings, including actionable remediation advice to help you secure your mobile app and prevent cyberattacks.

What vulnerabilities do we look for in a mobile application?
Our mobile application tests include the Open Web Application Security Project (OWASP) Top 10 mobile vulnerabilities as standard.
Our team uses a blend of advanced automated tools and manual expertise to uncover security weaknesses, which includes but is not limited to discovering:
- Improper platform usage
- Insecure data storage
- Insecure communication
- Insecure authentication
- Insufficient cryptography
- Insecure authorization
- Poor client code quality
- Code tampering
- Reverse engineering
- Extraneous functionality
Common mobile app vulnerabilities
Our team conducts thousands of penetration tests every year. Here are just some of the most common mobile application security weaknesses that we see across iOS and Android apps:
- Mobile certificate pinning
- SSL misconfiguration
- App Transport Security (ATS) disabled
- Application permission issues
- Hard-coded keys or credentials
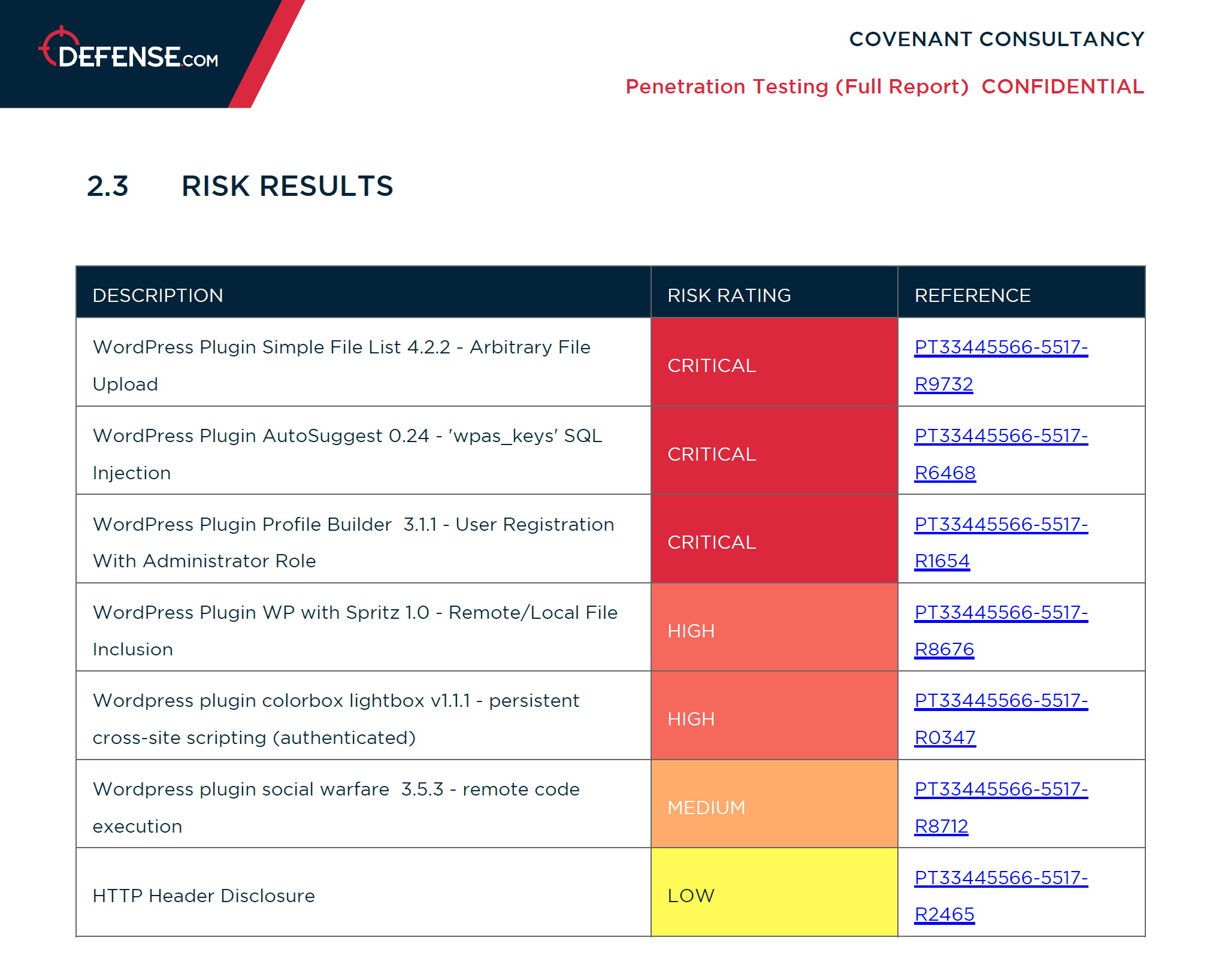
Your mobile app pen test report
When you get a penetration test with Defense.com™, your report is hosted in our secure web platform and will contain details about each vulnerability found during the test, along with actionable remediation advice.
In addition to your PDF report, you can use Defense.com™ to quickly identify, prioritize and manage each threat, saving you time and resources.
Get a quote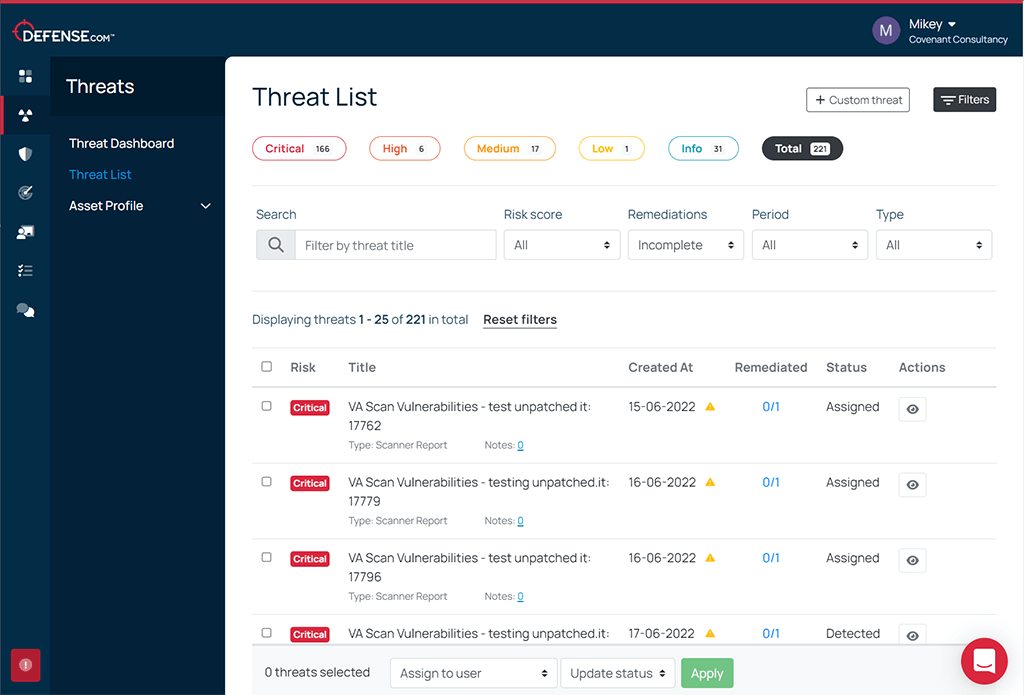
More than just a pen test
After your pen test you’ll also get 12-months access to extra tools in Defense.com™, including:
- Threat management tools to help you remediate anything identified in your pen test
- Vulnerability scanning for up to 5 IP addresses
- External attack surface monitoring to see your business through the eyes of a hacker
Alternatively, you can upgrade to a Defense.com™ Enterprise package to get even more features included alongside your pen test. Contact us to find out more and to get a quote.
Get a quote









Our penetration testing team
We pride ourselves on building and developing the best cyber talent to ensure our service is as evolutionary as the threat landscape. Our team of 30+ penetration testers are qualified against the leading industry standards and have years of experience delivering all types of penetration tests.
Mobile penetration testing methodology
Here’s what our customers say about us
Protecting the world’s leading brands
Get a quote today
If you’re interested in our services, get a free, no obligation quote today by submitting your requirements via the form below.
Frequently Asked Questions
The ‘always on’ nature of mobile apps and unprecedented data processing needs make them an attractive target for cyber criminals. Releasing a mobile application with cybersecurity risks could have a massive impact on your reputation and bottom line. As such, it’s important to regularly test your mobile apps for any weaknesses or vulnerabilities that could be exploited.
Yes, our team is experienced in both iOS application penetration testing and penetration testing apps for Android devices. We can provide you with a detailed report showing all of the vulnerabilities in your app, which gives you the opportunity to fix them before they are exploited by hackers.
- Small apps: 2-3 days
- Medium apps: 5-10 days
- Larger apps: 10 days+
All tests are scoped on an individual basis, so this should only be considered as a rough guide.
esting can be performed against a non-production replica of your app, such as a UAT/QA environment, to ensure no risk to your live services. If testing against production is unavoidable, we can coordinate our testing activities to minimise the impact. You can also specify things like no denial of service (DoS), meaning tests will have a negligible impact on your day-to-day operations.
Regular and comprehensive assessments of your cyber security are always recommended. The ramifications of security breaches can result in severe financial and reputational losses. We would always advise the safest approach is to regard your cyber security holistically as weaknesses in one area may undermine security implemented elsewhere.
Get a quote
Detect cyber threats and improve your security with our managed SIEM service.
