79% of companies have experienced at least one cloud data breach.
43% have reported 10 or more breaches.
Identify cloud security vulnerabilities
A cloud security assessment is the best way to safeguard your business operations in the cloud and enhance your cyber resilience. Our cloud penetration tests will:
- Uncover insecure functionalities in cloud environments such as AWS, GCP and Azure
- Expose weak access controls to your cloud bucket storage
- Reveal vulnerabilities in your cloud infrastructure security perimeter
- Improve security throughout your software development lifecycle
Your CREST-certified penetration tester will provide a full report with their findings, including actionable remediation advice to help you secure your cloud environment and prevent cyber attacks.

Get an expert cloud security assessment
All our cloud penetration tests assess your remote environment against the internationally recognized CIS security benchmark; however, we take this a step further.
Our expert pen testers conduct additional, bespoke manual checks which include reviewing lower-level configurations, secrets management, environment architecture, network segregation and IAM/identity privilege hardening.
Highlights from our AWS methodology includes (but is not limited to):
- Assess network segregation and external attack surface
- Review all permissions and authentication including database and storage
- Assess the security of your API Gateway applications and other such services
- Evaluate the effectiveness of your encryption
- Compare the account against industry best practices using the AWS CIS Benchmark
Common cloud pen testing vulnerabilities
Your cloud environment needs to be regularly assessed to identify security threats and give you a chance to fix them before they are exploited.
Here are some of the most common vulnerabilities we see and actively check for when conducting cloud security risk assessments:
- Exposed cloud storage instances
- External data sharing
- Vulnerable interfaces and APIs
- Overly permissive user roles & policies
- Server-side Request Forgery (gaining cloud credentials through an exposed web app)
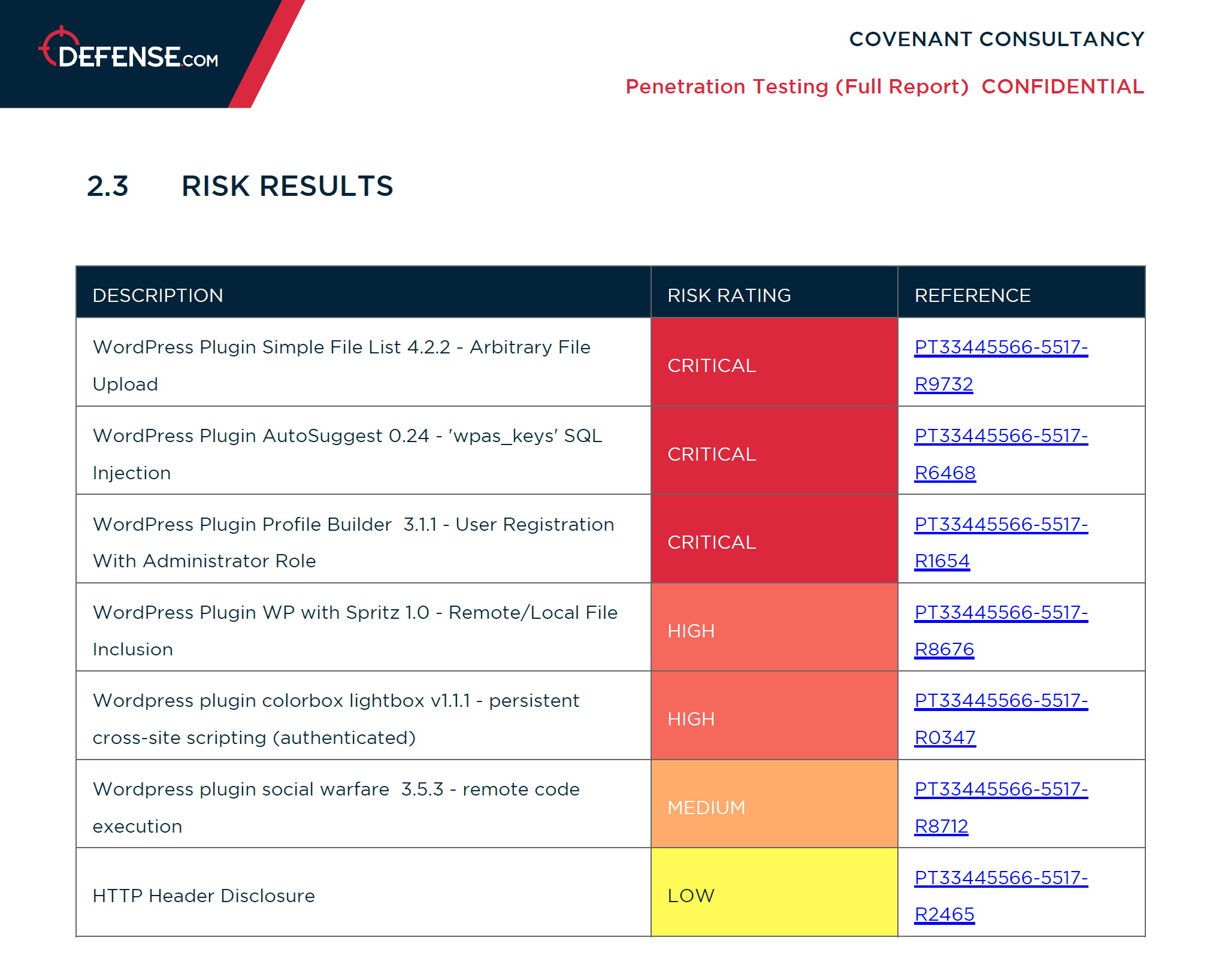
Your cloud pen test report
When you get a penetration test with Defense.com™, your PDF report will be hosted in our secure web platform. This will show each vulnerability found during your test, including actionable remediation advice.
You can also use Defense.com™ to quickly identify, prioritize and manage individual threats, saving you time and resources.
Get a quote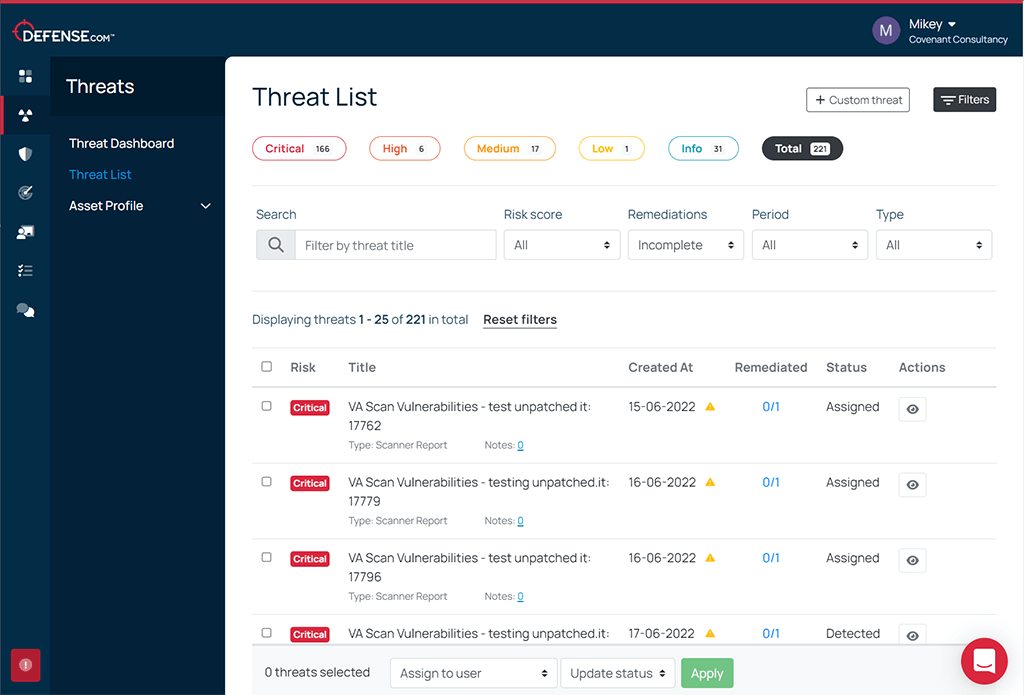
Get more than just a pen test
Having a pen test is an important part of any cyber security strategy, however it is only a point-in-time assessment.
When you get a cloud pen test with Defense.com™ you’ll also get free access to tools to help you manage your security over time:
- Threat management tools to help you remediate anything identified in your pen test
- Free vulnerability scanning for up to 5 IP addresses
- External attack surface monitoring to see your business through the eyes of a hacker
Alternatively, you can choose a Defense.com™ Enterprise package to get even more features included alongside your pen test. Contact us to find out more and to get a quote.
Get a quote









Our penetration testing team
We pride ourselves on building and developing the best cyber talent to ensure our service is as evolutionary as the threat landscape. Our team of 30+ penetration testers are qualified against the leading industry standards and have years of experience delivering all types of penetration tests.
Cloud penetration testing methodology
Most penetration testing follows a 6-step lifecycle:
Here’s what our customers say about us
Protecting the world’s leading brands
Get a quote today
If you’re interested in our services, get a free, no obligation quote today by submitting your requirements via the form below.
Frequently Asked Questions
Given that cloud networks are exceptionally attractive to cyber criminals due to the amount of data they hold, regular penetration testing is strongly advised. One or two times a year is usually enough to see how your security perimeters are faring against new attacks and to assess if new configurations have created any security weaknesses.
A cloud security assessment usually takes up to 7 days for smaller tests and over 7 days for larger tests. The amount of time needed will depend on the size of the environment and the extent of the test. Each cloud pen test is scoped on a bespoke basis, and you will receive a full breakdown of the activities and timeframes before committing to your test.
Your penetration tester will provide you with a list of all vulnerabilities found during your cloud penetration test, including how they could be exploited.
Your test results will be hosted in our secure Defense.com™ platform and automatically sorted in order of criticality. You’ll then have a prioritized list of vulnerabilities to fix, along with actionable advice to help you remediate each threat.
Cloud security audits are performed using read-only accounts wherever possible, as this minimizes the risk of the assessment having any impact on the target environment. These reviews are usually performed on production accounts as the checks involved are non-intrusive.
Due to this, cloud reviews have the benefit of being able to provide a level of security assurance for the live/production environment as opposed to any staging/QA systems. We can also coordinate our testing activities to minimize the impact further if need be.
Regular and comprehensive assessments of your cyber security are always recommended. The ramifications of security breaches can result in severe financial and reputational losses. We would always advise the safest approach for a company is to think about your cyber security holistically, as weaknesses in one area may undermine security implemented elsewhere.
As part of your penetration test with Defense.com you will get access to Vulnerability Scanning and an external attack surface assessment (Threat Recon). This will help you to identify any known vulnerabilities in addition to anything found during your pen test.
Get a quote
Detect cyber threats and improve your security with our managed SIEM service.
